

Welcome to the Hardenize blog. This is where we will document our journey as we make the Internet a more secure place and have some fun and excitement along the way.
“What’s running on our assets?” is often the next question our customers ask once they’ve successfully built an inventory of their domains, hosts, certificates, IP addresses, and cloud resources that is kept up to date continuously and automatically. To help our customers answer this, we’re delighted to announce Technologies V1 which is available now at no additional charge to paying customers. READ MORE »
Our existing customers have had early access to the first version of our cloud integrations feature for a while now. We're pleased to announce our next iteration of cloud integration monitoring that provides seamless monitoring of all public cloud resources. READ MORE »
In our release today, we added support for audit logging, a key feature for anyone who wants to have a good insight into the key events taking place in their account. An audit log is a stream of records that are emitted as various activities take place. These records are immutable and serve as a reliable record of events. Most organisations will care about the events that are related to user authentication and authorization, and those that change the state of their accounts. READ MORE »
We’ve been working closely with our friends at Infobalt, the Lithuanian digital technology sector association, to build our latest public dashboard and I’m delighted to announce that it’s now live. READ MORE »
We're very happy to share with you that we're joining Red Sift, a like-minded cybersecurity company whose main focus is on email and domain name security. Hardenize and Red Sift will combine their respective efforts to offer a suite of products designed to help organizations of all sizes secure their network and application infrastructures from the ground up. Hardenize's discovery capabilities will immediately help Red Sift's existing customers by providing better visibility. Red Sift's mature organization will help bring Hardenize's platform to the market as well as accelerate development of new capabilities. READ MORE »

We continue to add new integrations with parts of the supply chain that contain data that will help our customers to maintain an asset inventory automatically and continuously. Today, we’re announcing two new Hardenize integrations with domain registrars: CSC and Safenames. READ MORE »

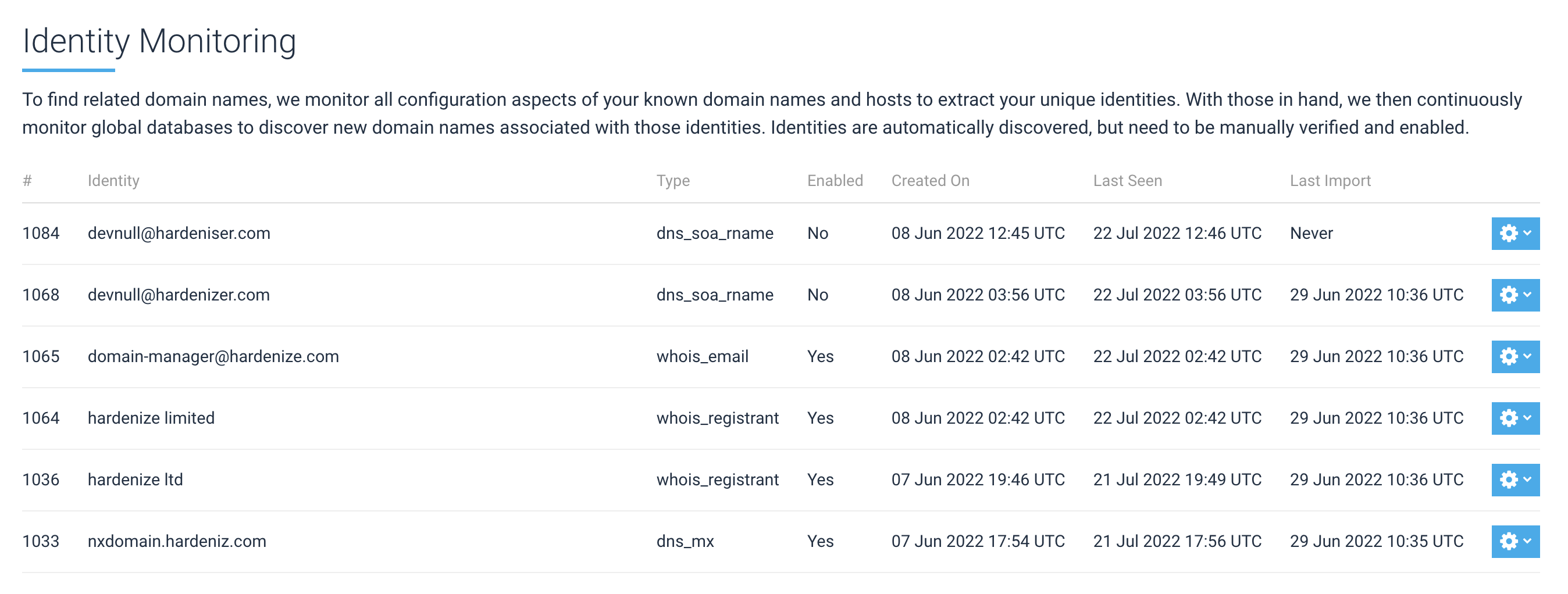
Today we're announcing Related Domain Discovery, our new functionality that uses a variety of big-data sources to automatically discover new domain names connected to the domain names already in customer accounts. With this improvement, we make it even easier for our customers to find and keep an eye on their network and application infrastructure. READ MORE »
Continuing to expand on the theme of integration with our customers' infrastructure, we're announcing support for discovery via continuous DNS zone transfer. With this new feature, we can ensure 100% visibility into all zone hosts and resource records. READ MORE »
When it comes to network infrastructure, both security and availability begin with domain names. You can have the best security elsewhere, but if your domain name is taken away from you, it all falls apart. With today’s release, we’re adding domain name registration monitoring to our capabilities. READ MORE »
In the early days of Certificate Transparency there weren’t many CT log operators, which compelled Google to require that all certificates are logged to at least one Google-operated log. Starting in March 2021, Chrome deployed and continued to improve SCT auditing, which aims to provide additional security no matter where the certificates are logged. From April 2022, Chrome will use a new CT policy that removes the “One Google Log” requirement. READ MORE »
For us, TLS and PKI are where it all started. Hardenize is actually a continuation of our long-term effort to understand network and security protocols at a deep level, as well as build the best possible tools to use them. To that end, we’re happy to announce the release of the second edition of Bulletproof TLS and PKI, a comprehensive and practical guide to these important internet standards. READ MORE »

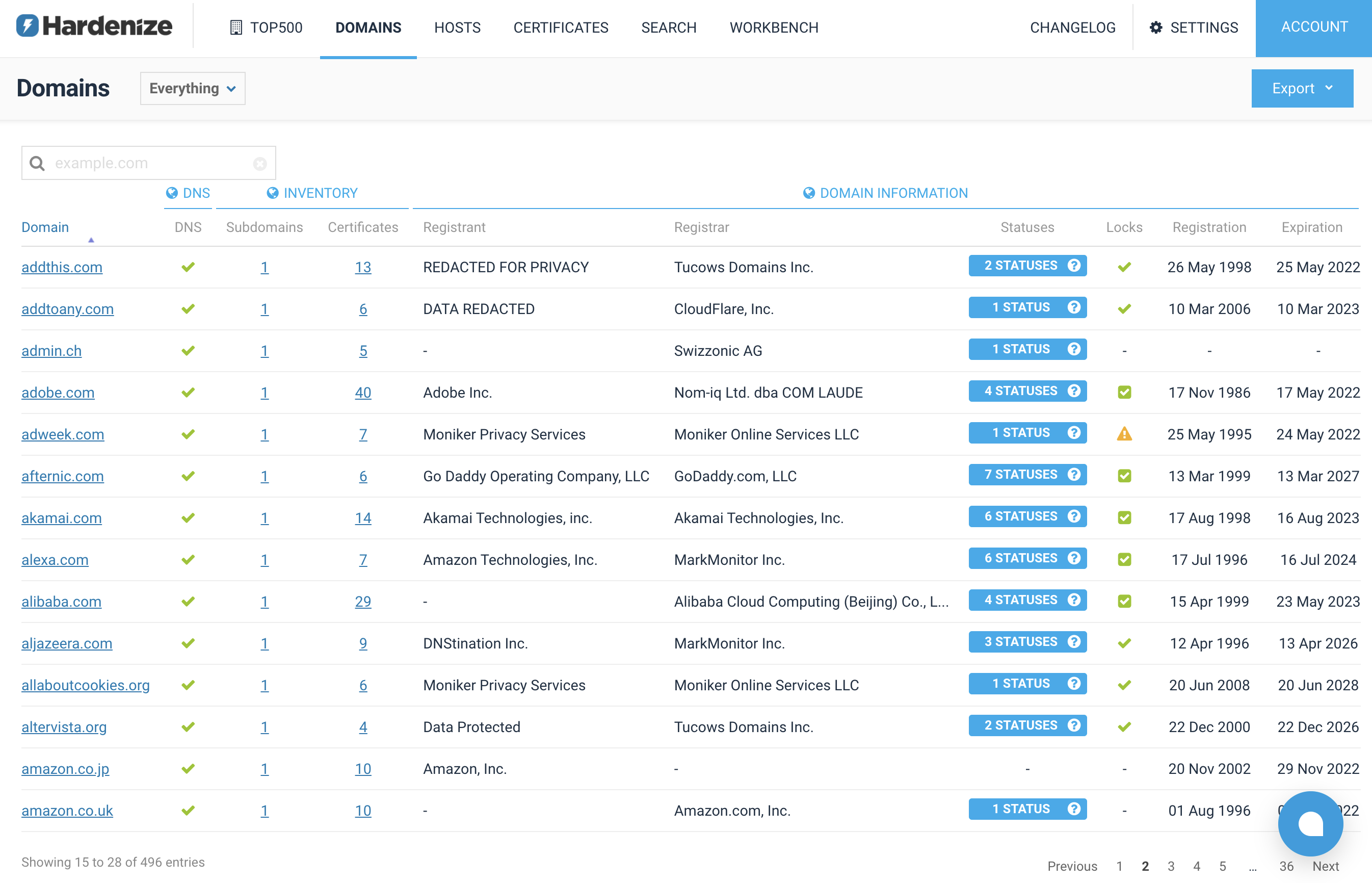
The only way that organizations can effectively monitor their network and apply the appropriate security standards is if they have a good inventory of their assets. As that is difficult to do because assets reside in many different places, an important part of our recent development work has been integrations with third-party platforms. Today we’re announcing three new integrations: Cloudflare, MarkMonitor, and NS1. READ MORE »

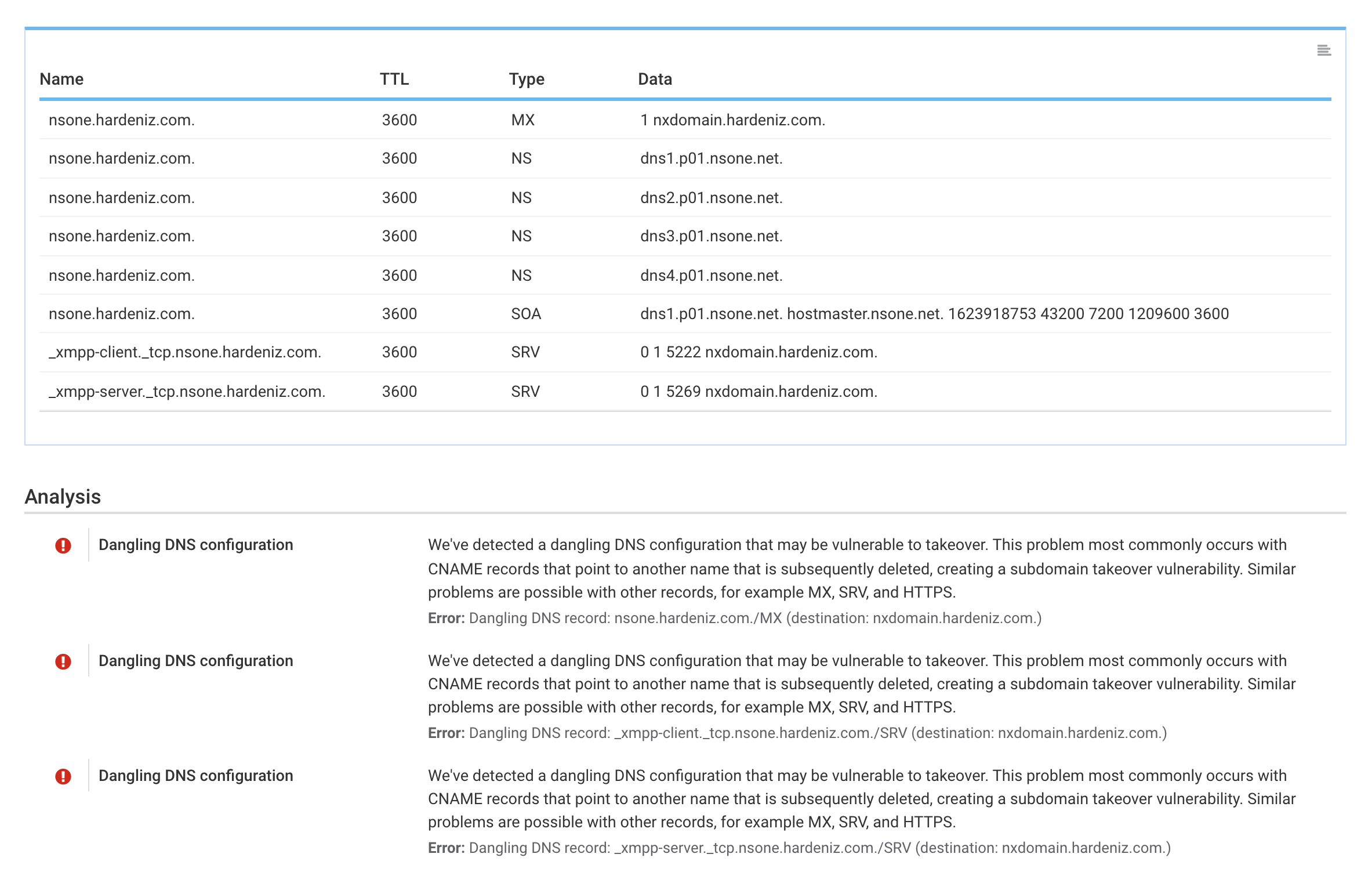
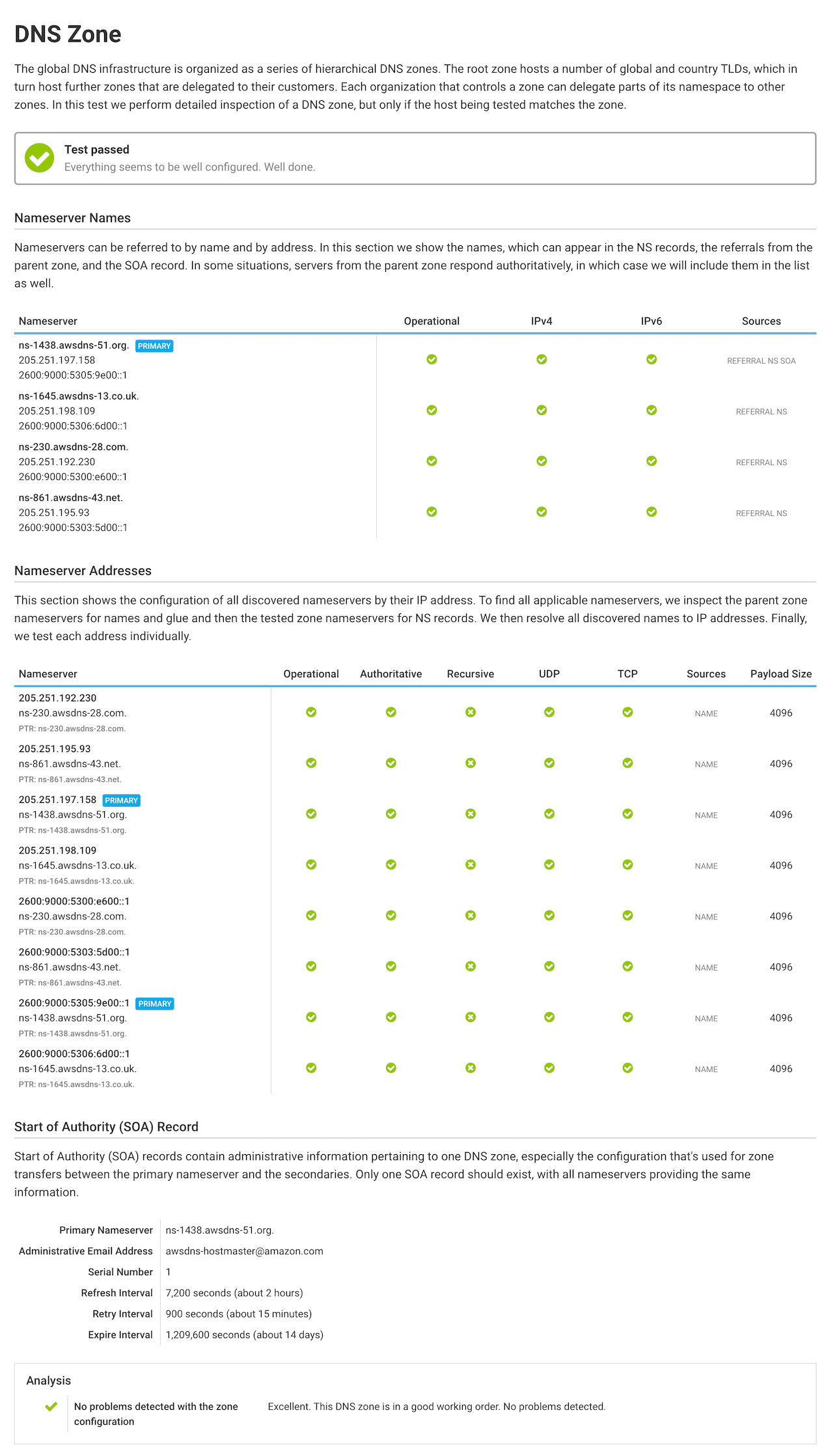
Last time, we announced the addition of comprehensive DNS inspection to Hardenize. Building on that foundation of being able to reason about DNS configuration, today we continue our deep dive into DNS with automatic detection of a range of dangling DNS issues, helping organizations keep their DNS configuration clean and prevent domain and subdomain takeover attacks. In this blog post we discuss what aspects of DNS lead to dangling DNS issues, enumerate a number of practical problems, and show how we address them in Hardenize. READ MORE »
It’s our great pleasure to announce that we have added support for DNS inspection to Hardenize. This new functionality is now available in beta as part of our public report and for all our customers. In our first release we’ve focused on the inspection of DNS zone configuration and delegation, the parts that are necessary to provide highly available and consistent name resolution. READ MORE »
This year, one of our main development directions is around third-party integrations. A couple of months ago we announced our phase one integration with the major cloud providers: AWS, Azure, and GCP. Today we’re happy to expand our capabilities with an integration with DigiCert CertCentral, our first with a Certification Authority. With this new release, joint Hardenize and DigiCert customers can benefit from having an additional view into their certificate inventories. READ MORE »

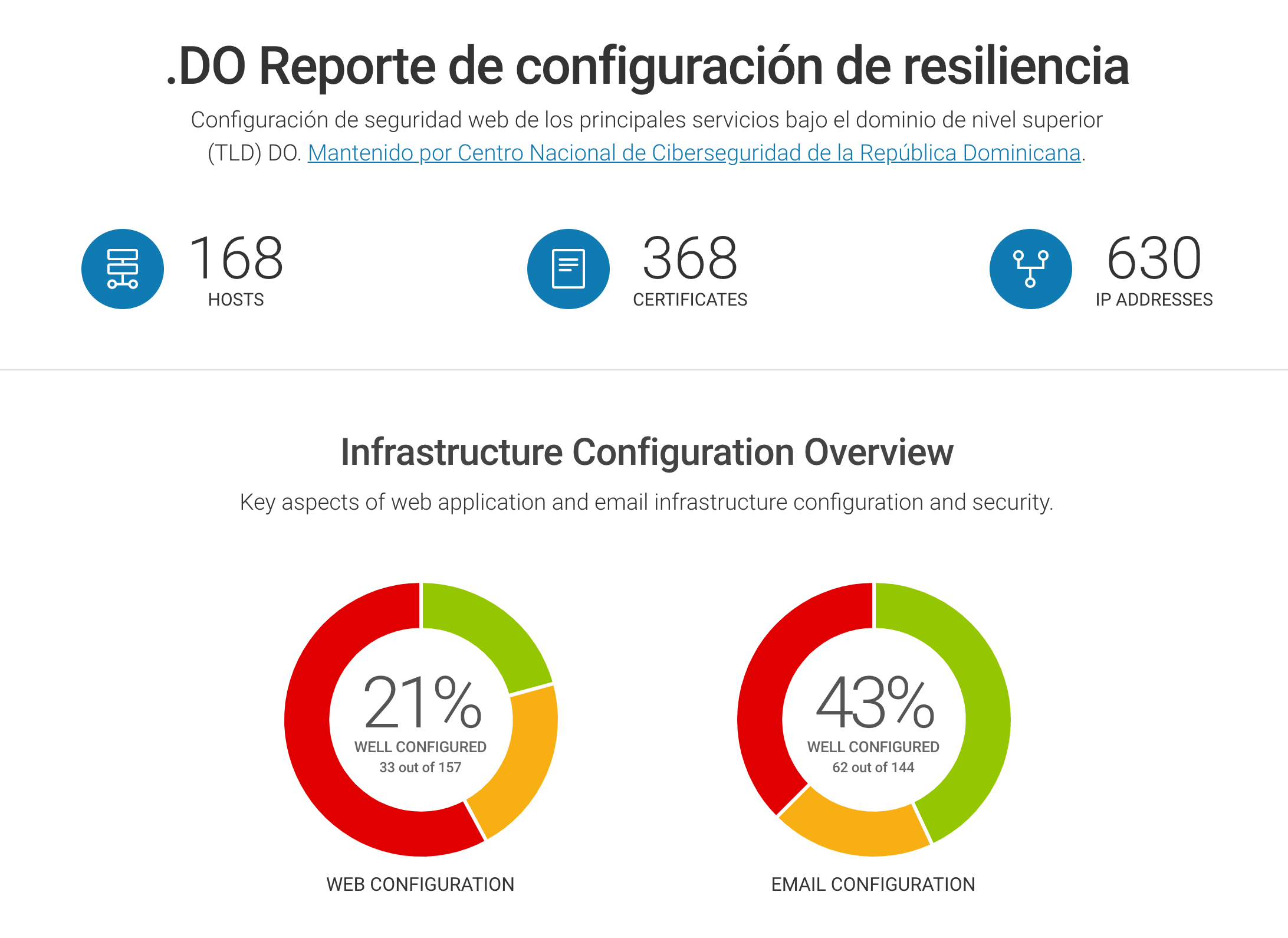
We’re delighted to publish our fifth official public dashboard for the Dominican Republic and the .do top-level domain. This latest dashboard has been built in collaboration with our friends at the National Cybersecurity Center of the Dominican Republic, CNCS. CNCS created this dashboard because they want to take the results to the owners of the main services and work with them to improve their security configuration. READ MORE »
It’s a very special day for us at Hardenize because, with today’s deployment, we’re open for business. The waiting list is gone and our pricing has been revealed. Anyone and everyone who comes to our web site is able to request to try our product and—if the alignment of values is right—become our customer. We welcome you, and we’re looking forward to helping you navigate the maze that is network and application infrastructure security. READ MORE »
We couldn’t be more delighted to announce our brand new project. Hardenize Policy is our effort to address the root causes of slow adoption of new security standards. We believe that the sheer number of available standards, their complexity, and the fast pace of change is a significant barrier for many. Hardenize Policy will provide a comprehensive guide to a wide range of network and security standards in a format that’s easy to consume. Our first instalment covers security of email infrastructure, with additional documents to follow. READ MORE »
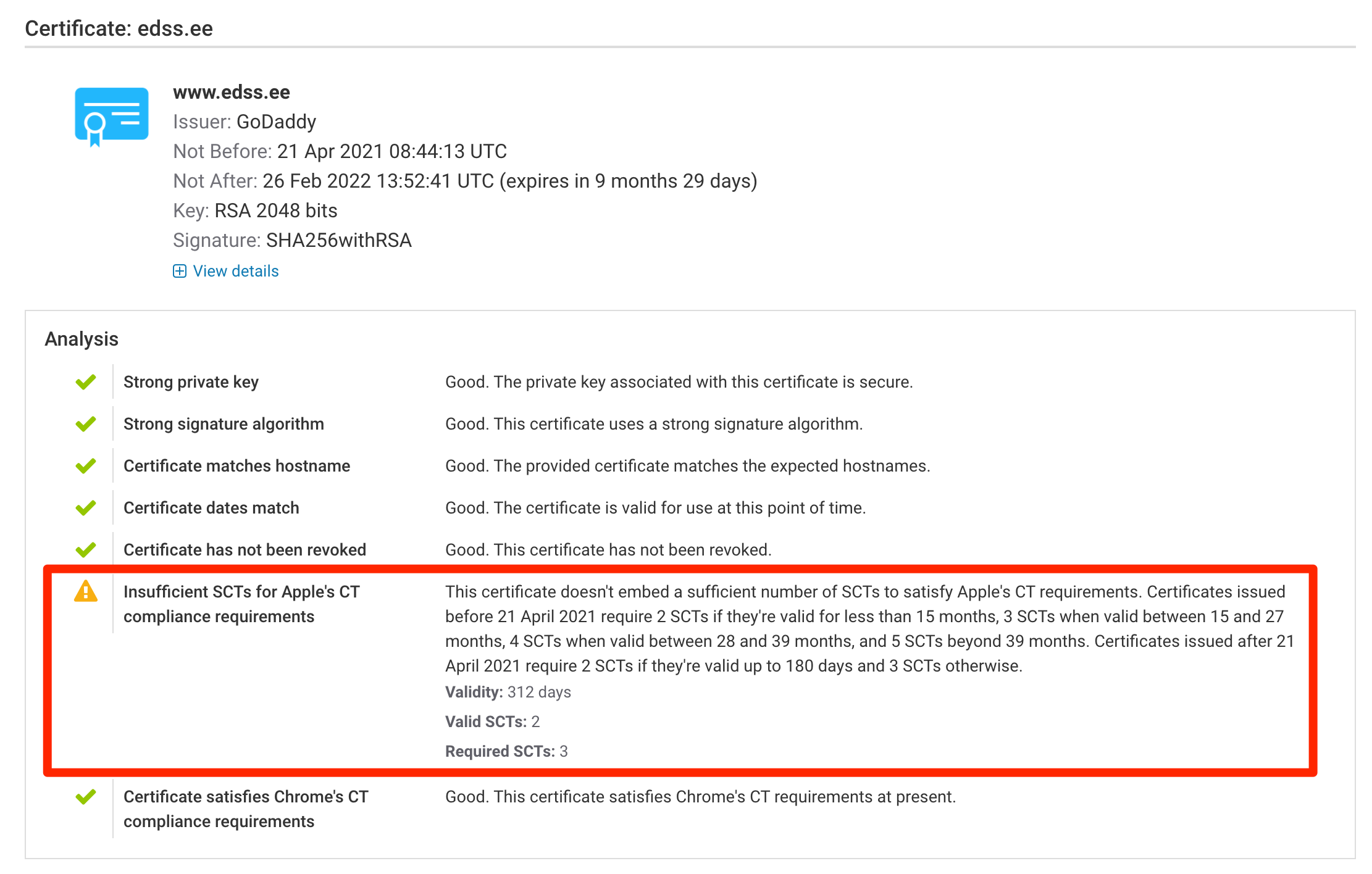
Certificate Transparency is a global and collaborative effort to continuously release new public certificates to the public and provide transparency of the inner workings on the public PKI infrastructure. Earlier this month, on 21 April 2021, Apple’s updated CT policy brought several important changes as well as introduced a divergence in CT requirements for public certificates. Not all CAs adapted to the new requirements in time. READ MORE »
Certificate Transparency (CT) continues to develop and improve at a good pace. A new feature called SCT Auditing has been in development for some time and is currently being deployed to Chrome. The auditing will provide better visibility into the correct operation of the CT ecosystem. READ MORE »
In the last couple of years, our focus at Hardenize has been on automated discovery of company assets based on large-scale monitoring and analysis of public infrastructure. This is the Hardenize you know and love: a small investment of your time yields big results. However, we have decided to go further. As part of our continuous quest to improve our discovery and asset inventory capabilities, we are expanding our capabilities with managed cloud account integration. We are delighted to make the first release of this feature available in Hardenize. READ MORE »



We’re delighted to welcome Billy McDiarmid to our team. As a startup, we’re very focused on helping our customers solve their problems, and that’s exactly where Billy comes in. We’re very happy to have him in charge of Customer Success.
I’m a technology geek and the favourite bit of my chosen career path is when I help a customer to achieve something using software that would have been difficult or impossible without it. That is why I was so excited by Hardenize; I could see clearly how the application makes life easier for development and security teams.
As the Hardenize team are experts in internet security, I knew that I would be able to learn so much and help to transfer that knowledge to our customers.
I too believe that everyone deserves good internet security and I’m looking forward to growing helping our customers as well as our free users achieve that.
Billy is an experienced customer and project manager and has been helping customers to achieve the best results from their technology for more than a decade.
Trust in the WebPKI is now easier than it was ten years ago. We have gone from a world where attacks against individual CAs can compromise the entire system without trace to a world where multitudes protect our trust. Much of this is thanks to Certificate Transparency (CT), a system that ensures that all public certificates are recorded in tamper-resistant storage.
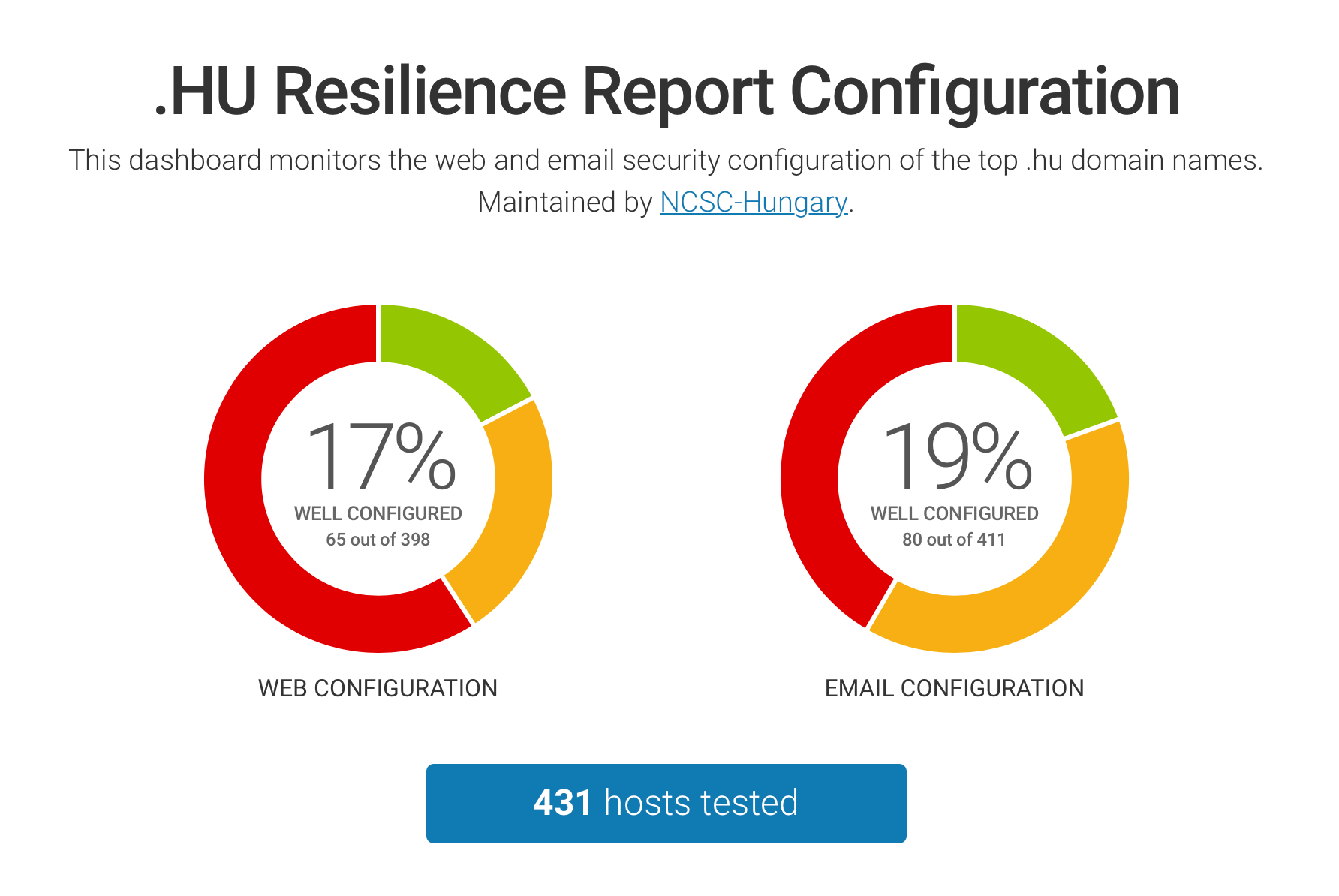
READ MORE »We are very happy to announce the addition of a new public dashboard covering top sites in Hungary. The dashboard is a collaboration with the Hungarian National Cyber Security Centre. Hungary is joining Sweden, Switzerland, and Estonia to become our fourth official dashboard. We remain committed to our goal to support official dashboards for all countries worldwide.
A number of intermediate CA certificates will be revoked because they were issued incorrectly. This means that all of the certificates issued by these CAs will no longer be trusted. If you have one of the affected certificates in production, you should plan to replace them as a matter of urgency. This issue was first reported by Ryan Sleevi on July 1st; according to the Baseline Requirements, the CAs are obliged to act within 7 days. READ MORE »
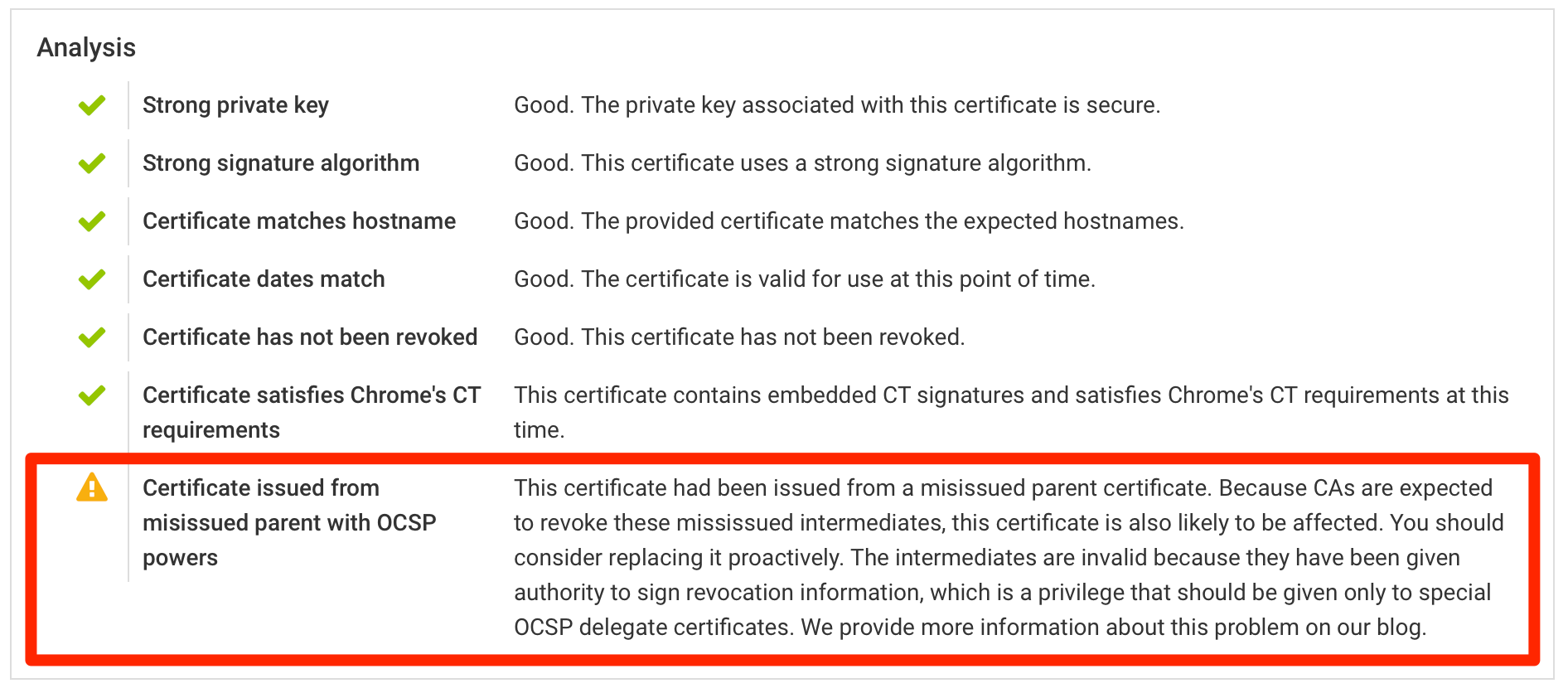
Update (1 September 2020): As of today, certificate lifetimes are restricted to 398 days. Ballot SC31 of the CA/Browser Forum, passed on 16 July 2020, formally adopted the changes described in this post and incorporated them into Baseline Requirements.
Apple have changed the rules their software uses in deciding which certificates to trust. Certificates issued from 1st September can have a lifetime of only up to 398 days. From that point in time, certificates valid for longer periods will not be trusted at all. We are updating Hardenize to detect affected certificates as soon as they are published to Certificate Transparency. READ MORE »
It is our great pleasure to welcome Mark Goodwin to Hardenize. His presence will not only substantially expand our engineering team, but will also add key skills we need to further expand into application security. With Mark on board, we will be spending much more time in the application security space, diving into unexplored depths.
I worked with Mozilla for almost nine years. Nine years is a long time in tech. That I stayed so long says much about Mozilla; it’s a hugely influential organisation with a vital mission and excellent people. That I chose Hardenize when the time came to leave says much too; I’ve been impressed by the commitment to build a product that helps everyone and the focus on improving the ecosystem. I’m excited both by what I can bring to this company and what we’ll do together.
Mark is an experienced information security specialist with many years of expertise building and breaking software security. He comes to Hardenize from Mozilla, where he worked as Staff Security Engineer and Mozilla’s UK Country Ambassador.
Hardenize began with hostname-based scanning, meaning we would build an inventory of domains and subdomains—mostly via our automated discovery—then continuously monitor the IP addresses behind the known names. That actually works very well, especially given the rise of virtual hosting, where many services can be hosted on the same port but with different configuration. This is critical, for example, for our ability to discover all deployed certificates. Although name-based scanning has served us well, in order to further improve the visibility of our customers’ systems, we’ve now added support for traditional network scanning. READ MORE »
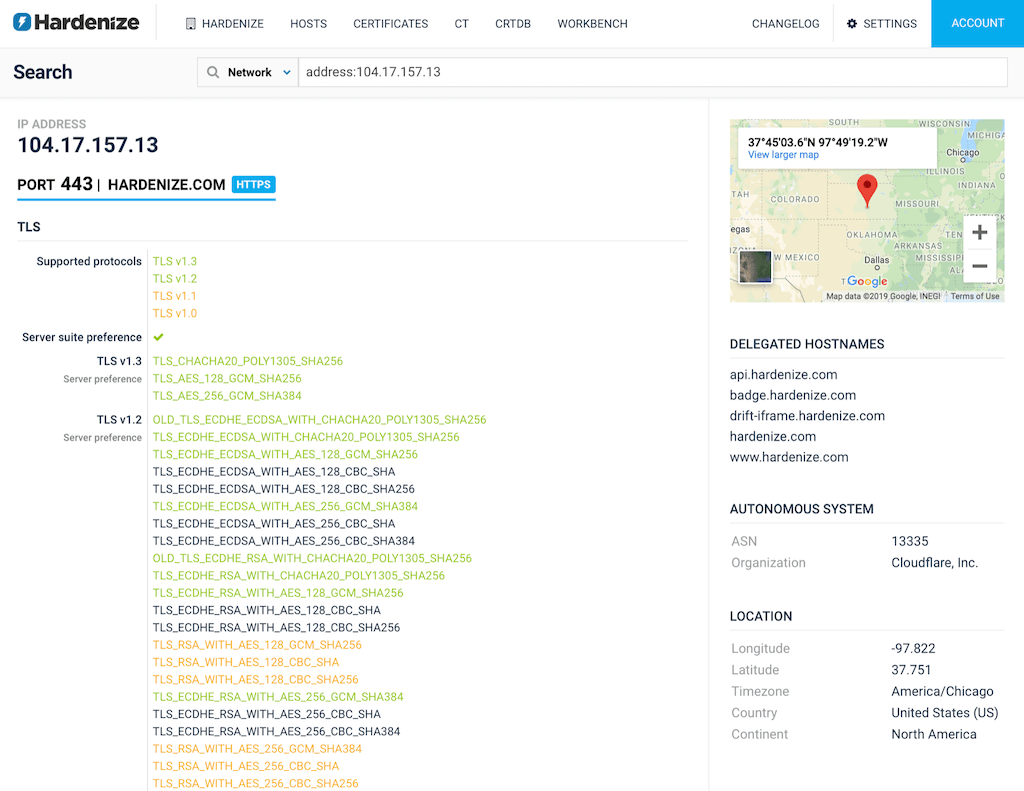
We’re very happy to announce our new distributed monitoring platform, a project we’ve been working on for some time. In the past year, as we started to onboard more customers and especially the bigger ones, we determined that we need a worldwide monitoring presence to adequately cover our customers’ infrastructure. As you may know, Hardenize has strong support for TLS and PKI; this new platform will help us on our path to reliable and comprehensive certificate monitoring of complex network architectures. READ MORE »
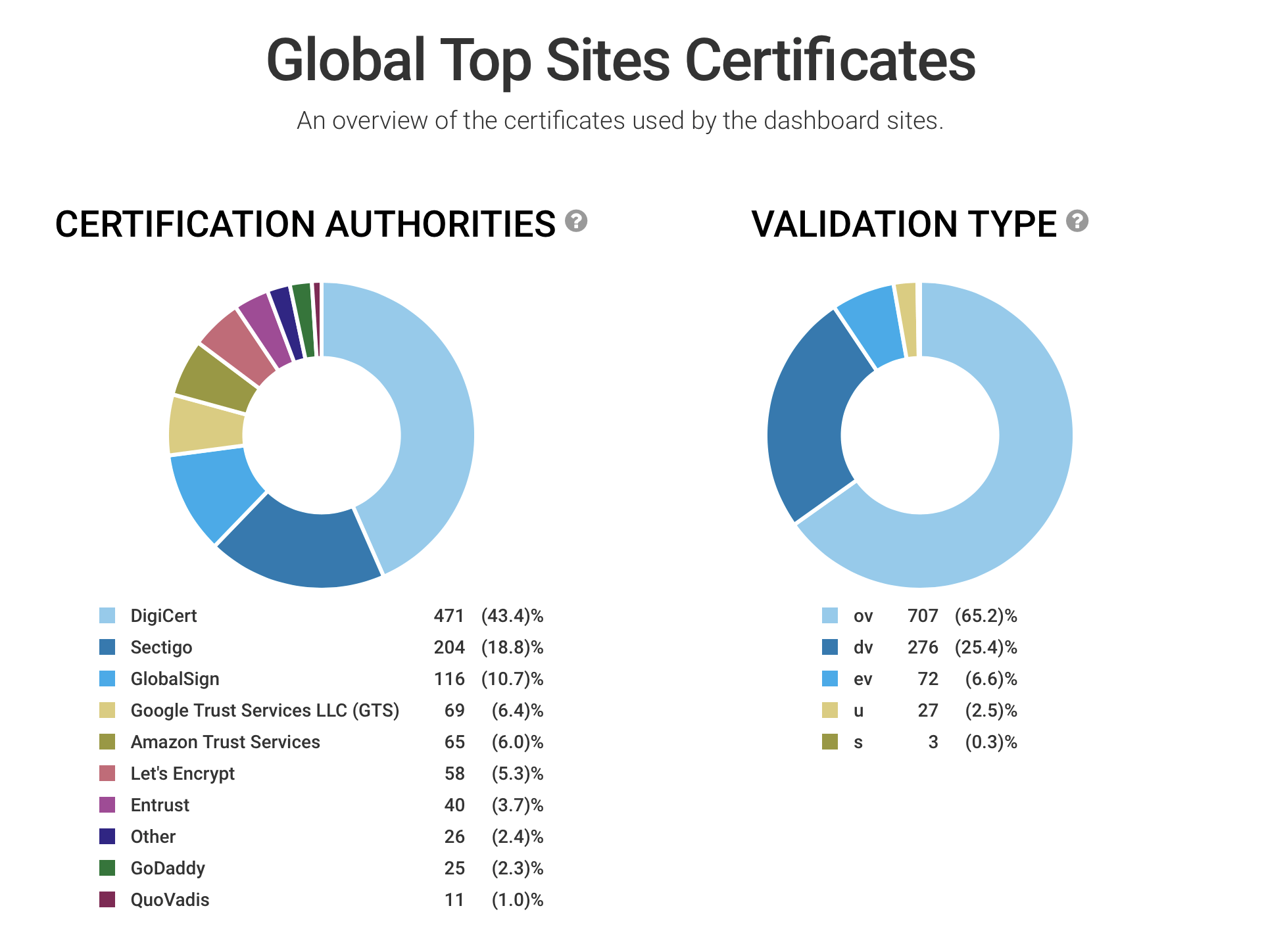
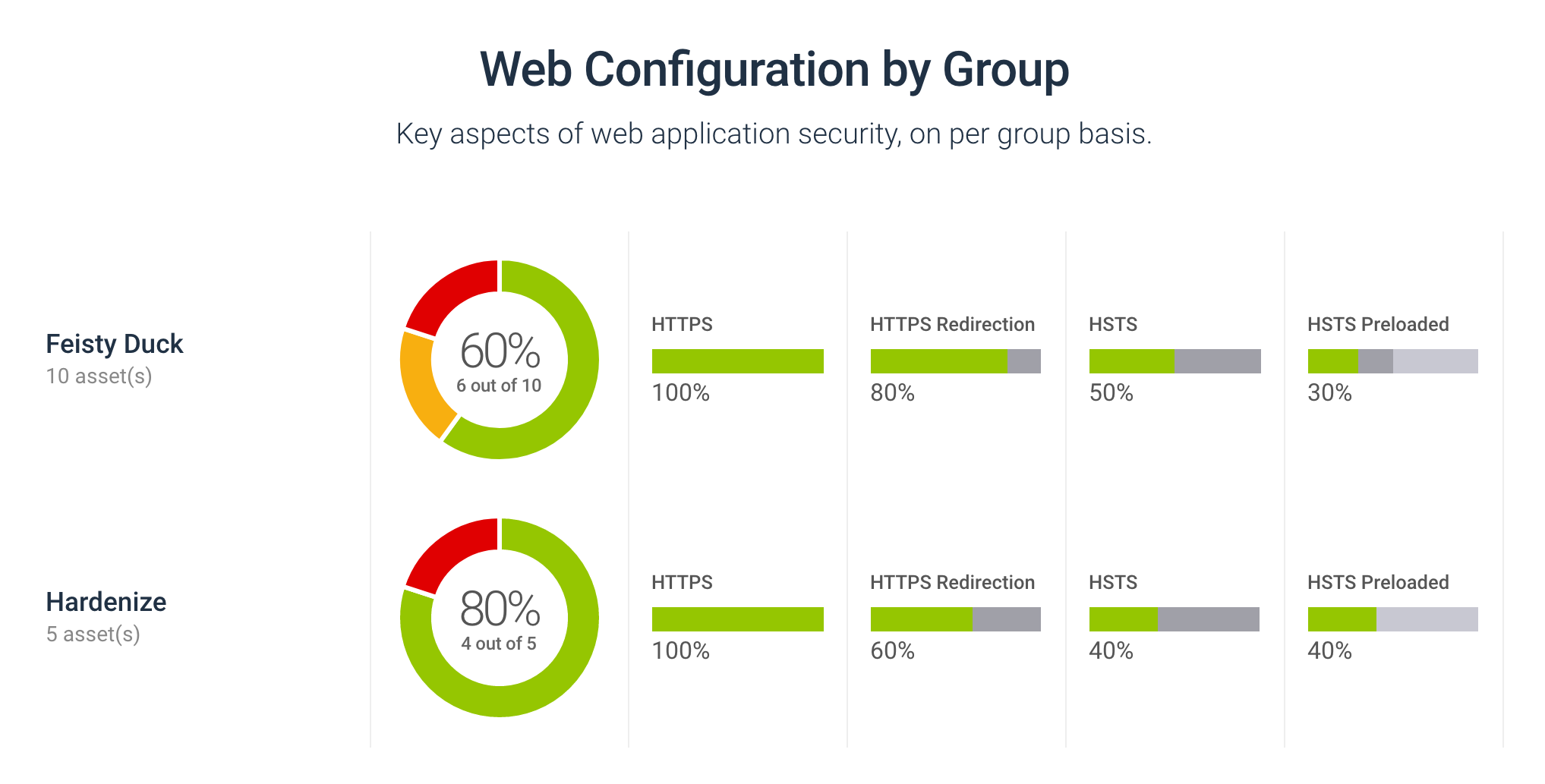
As you probably know, we love our public dashboards, as they are a great tool to quickly gain insight into the security posture of a group of web sites. Today we’re taking the dashboards further by extending them with statistics about certificate usage. From any dashboard page, simply click on the "PKI" navigation link to see exactly that certificates are being deployed. READ MORE »
In our earlier blog post, we wrote about our research on detecting phishing hostnames in certificates obtained from Certificate Transparency logs. Today, we’re taking our efforts further with the release of our project for automated discovery of phishing hostnames based on the continuous monitoring of all public certificates. This project is also the first to feature in our new Labs section, which we will use to publish our research. READ MORE »
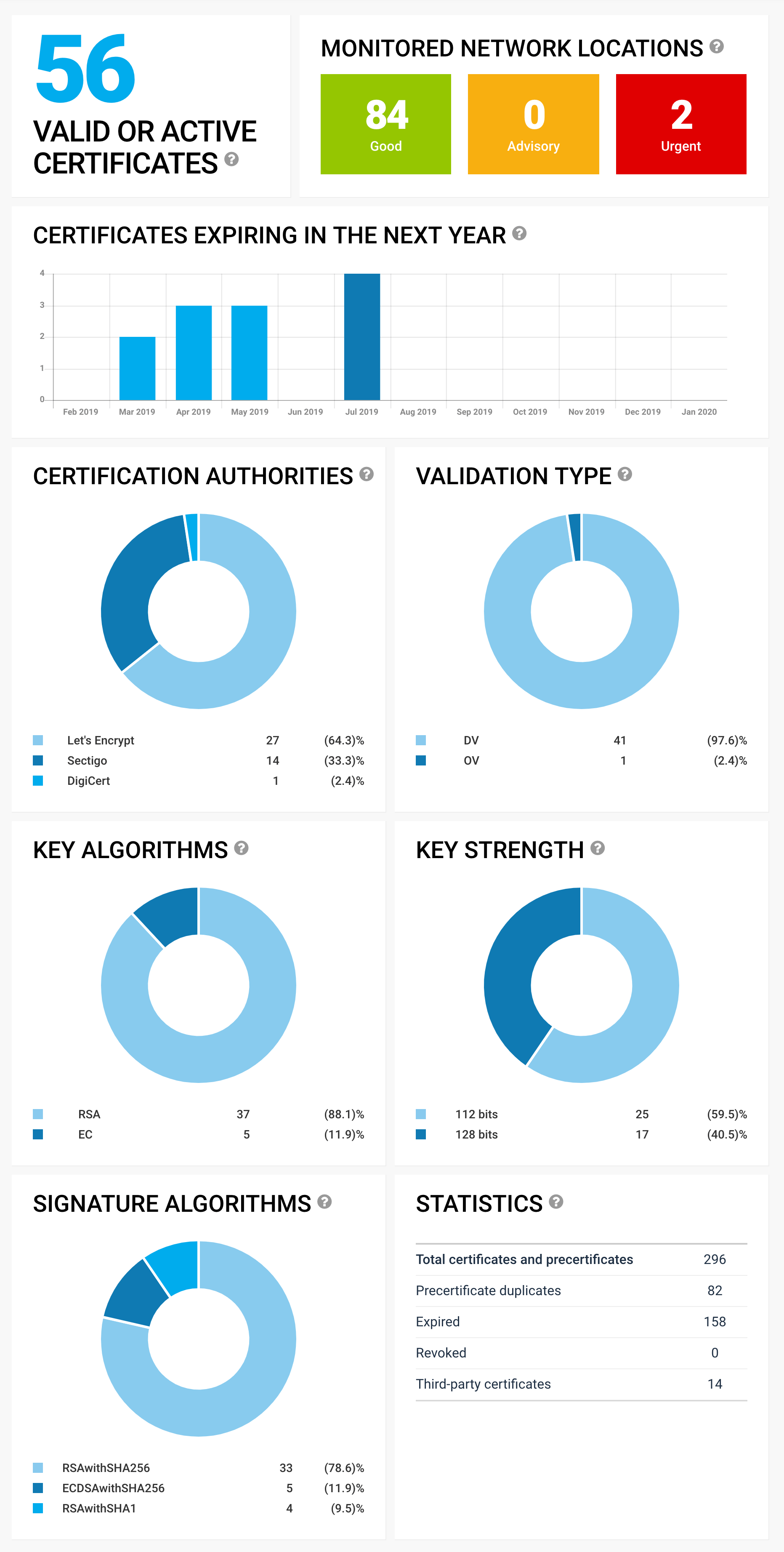
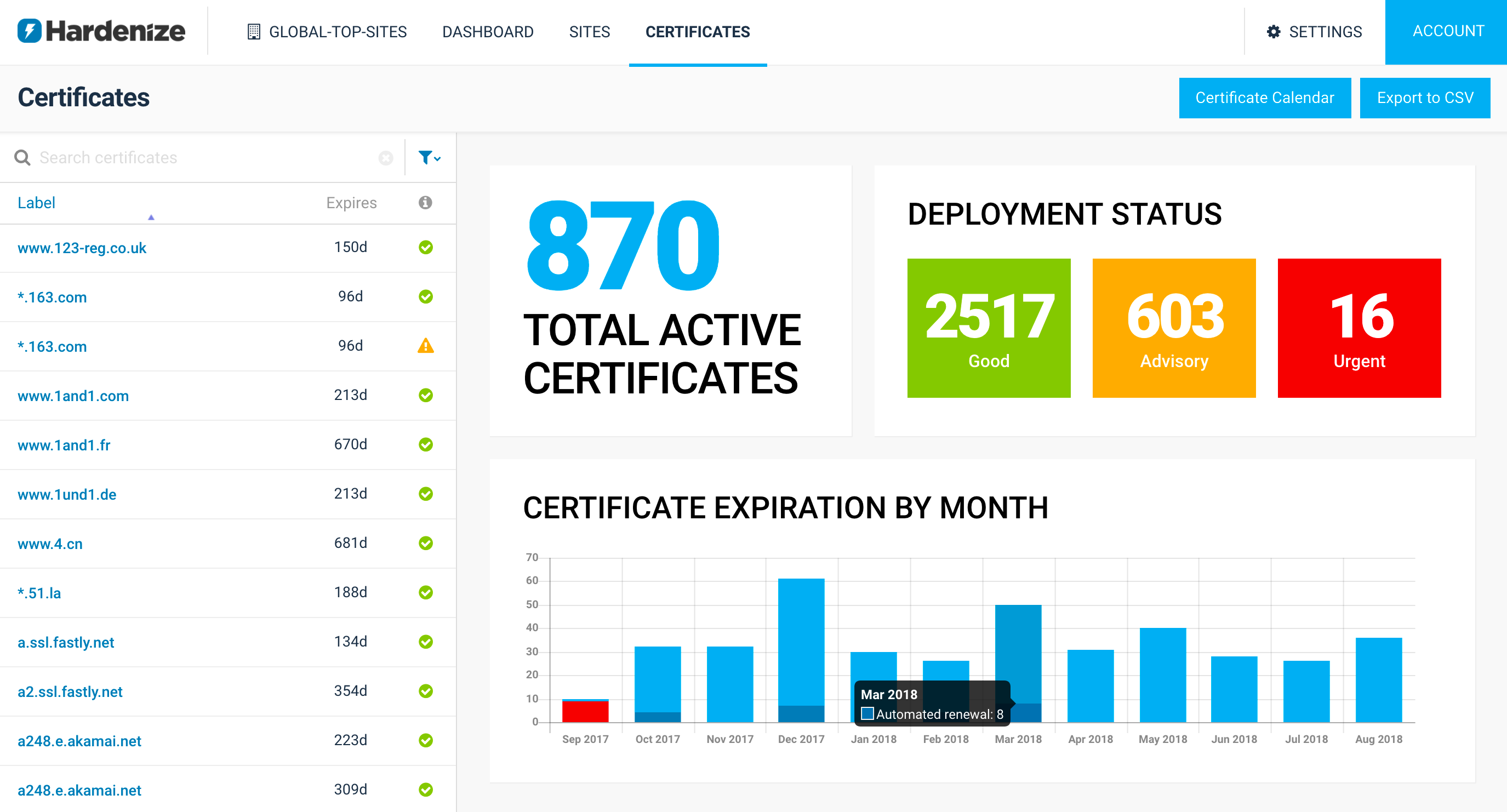
Our old certificate dashboard has served us well, but we’ve now released a brand-new, updated, certificate dashboard. Our new dashboard for certificate monitoring has been designed to give show you—at a glance—the key parameters of your certificate inventory. READ MORE »
As you’re probably already aware, phishing is a type of social engineering attack designed to lure users to web pages that look like legitimate web sites, but are actually phony setups designed to obtain their sensitive information. Certificate Transparency, which added auditability to the PKI ecosystem, is the latest tool in the fight to detect phishing sites reliably and quickly. The premise is simple: We monitor all public certificates and analyze every newly-discover hostname for signs of illegitimate intentions and otherwise indications of deception. READ MORE »
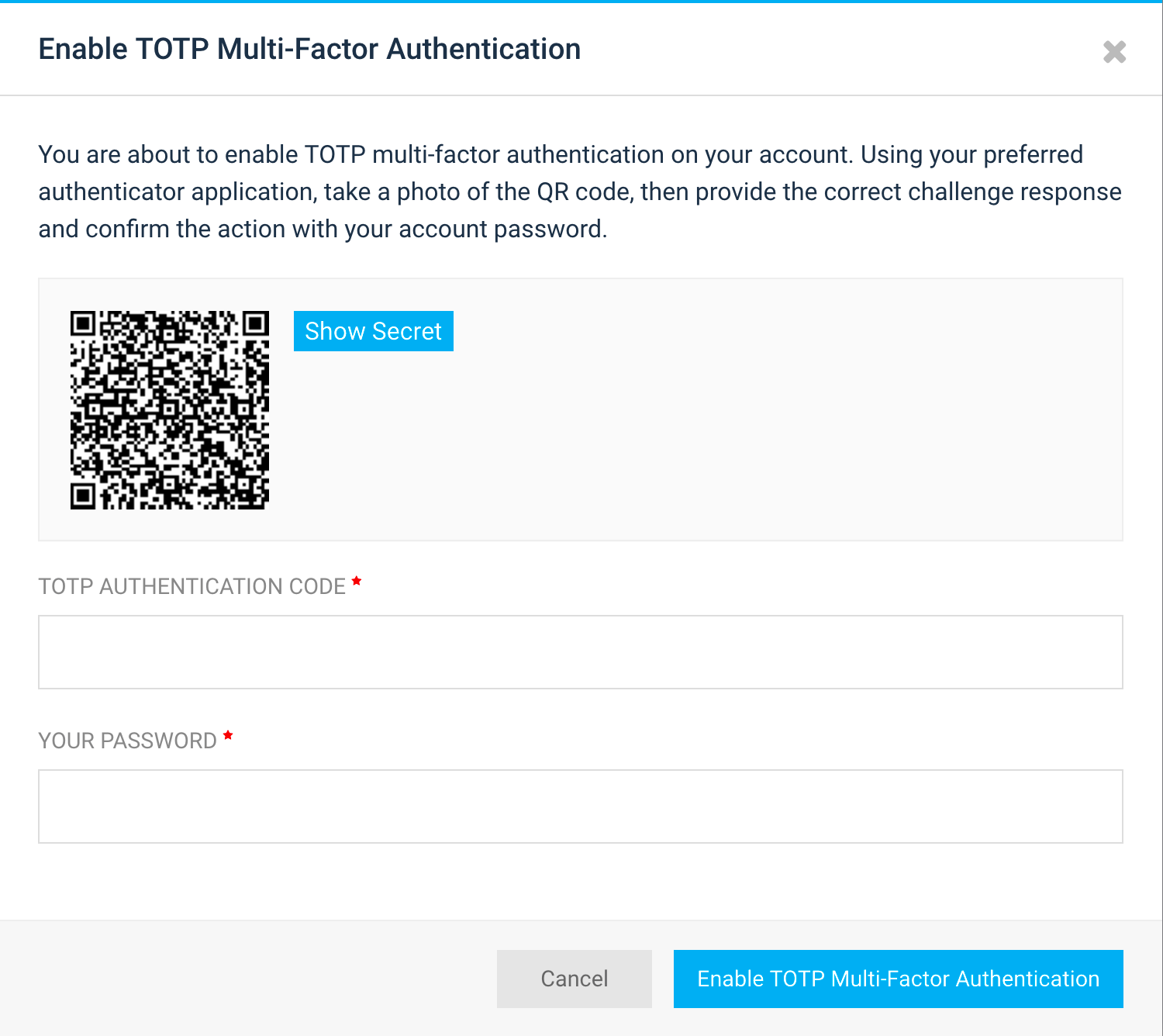
As we build Hardenize, we spend our time designing exciting new features, which we like to call delighters. However, we also pay attention to what other important functionality we need, where we usually heed advice of our customers. Our most recent feature is one of those. We’ve just added support for two-factor authentication. To be honest, we’re quite delighted to have it. So it’s a win-win! READ MORE »
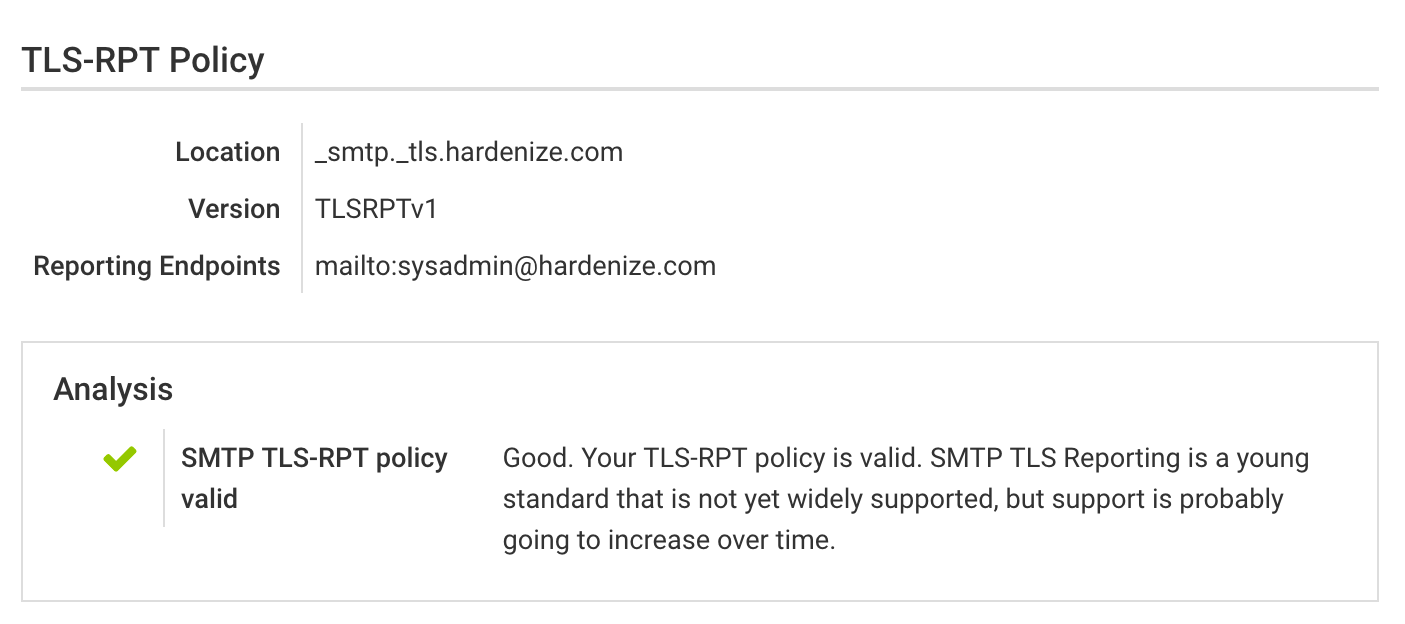
SMTP TLS Reporting (or TLS-RPT for short) is a new standard that enables reporting of TLS connectivity problems experienced by applications that send email. The standard is documented in RFC 8460, which was released in September 2018. We’ve extended Hardenize to look for and test TLS-RPT policies in all assessments. READ MORE »
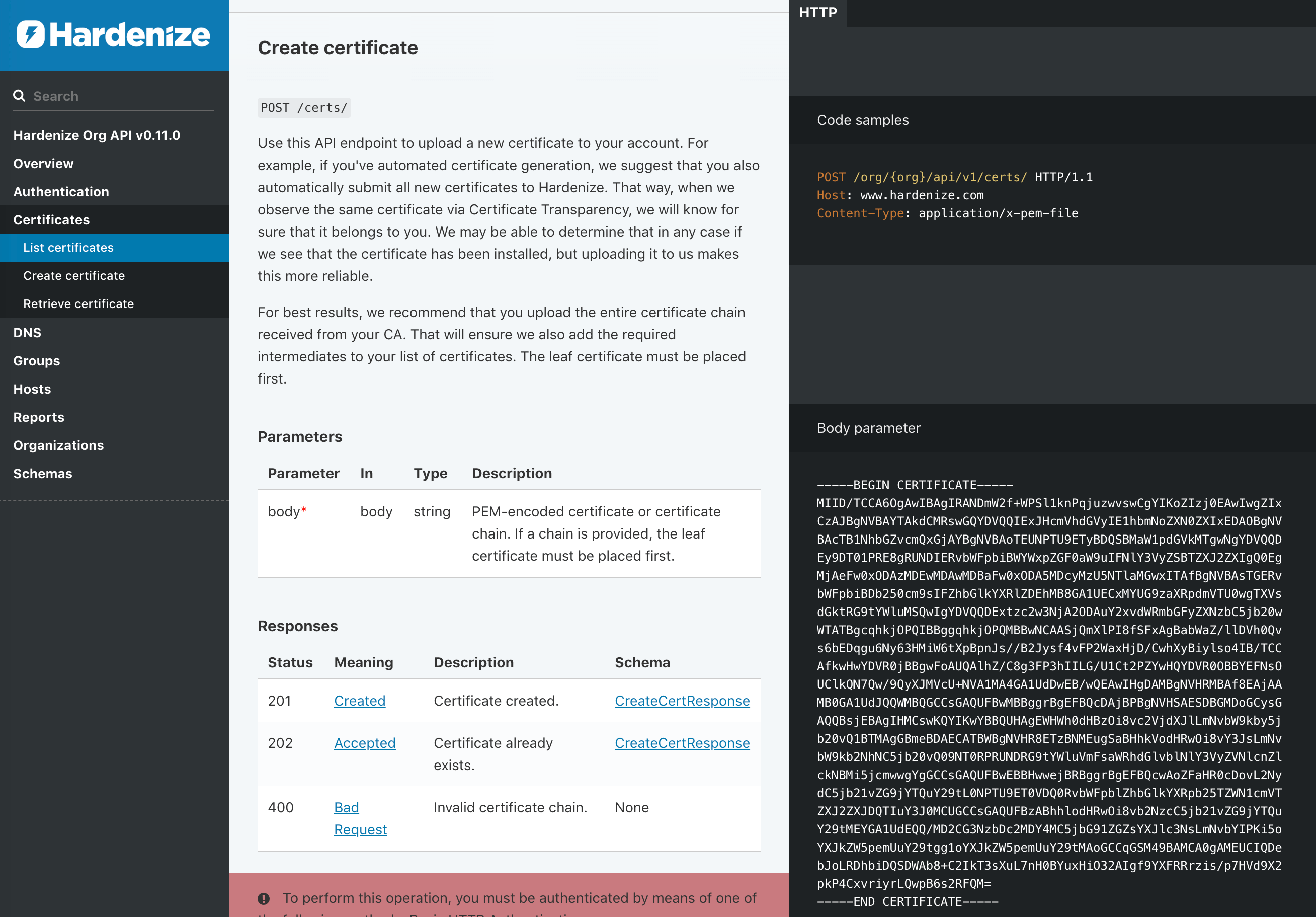
We’re continuing to develop our APIs; this month we extended our capabilities with Certificate Transparency events and webhooks, enabling our customers to receive programmatic real-time notifications of new certificates issued for their domain name space. READ MORE »
We’re happy to announce the first release of public Hardenize APIs, which enable our customers to have direct control over their accounts. The main focus of today’s release is to provide the essential API endpoints, as well as establish a strong foundation on top of which we will continue to build. Read on to hear more about our journey exploring various API approaches and how we (perhaps unsurprisingly) settled on REST. READ MORE »
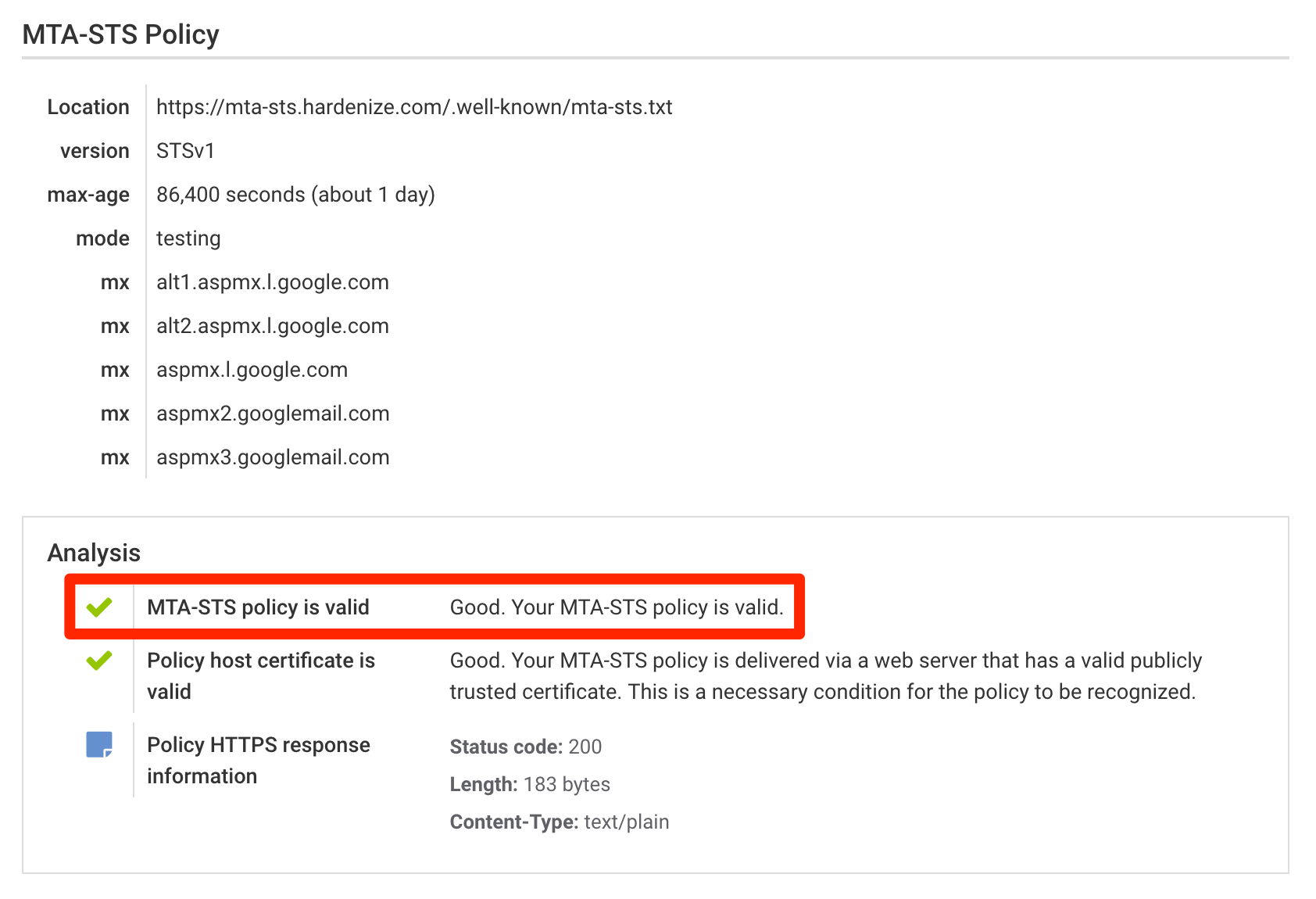
MTA-STS (the full name SMTP Mail Transfer Agent Strict Transport Security) is a new standard that aims to improve the security of SMTP by enabling domain names to opt into strict transport layer security mode that requires authentication (valid public certificates) and encryption (TLS). In this blog post we discuss why MTA-STS exists and how it’s used, as well as announce full support for its most recent draft in Hardenize. READ MORE »
We’ve just delivered our second batch of features intended to provide full support for the Certificate Transparency (CT) ecosystem. Chief among them is support for the Expect-CT HTTP response header, which sites can use to enable CT compliance enforcement and reporting. Additionally, we’ve also added a series of user interface and functionality improvements to test for edge cases and detect non-CT-compliant deployments. READ MORE »
When we set out to build Hardenize, one of our goals was to provide an almost-interactive experience, one where you don’t have to wait for a long time to get useful results back. We thus spent a lot of time making Hardenize fast. Unfortunately, even though our tests are lightweight and going fast works for HTTP, the approach breaks completely in the SMTP land, where we were often being blocked. To fix that, we went back to the drawing board and completely redesigned how we test SMTP. READ MORE »
After April 30th, Chrome will start rejecting all new certificates that don’t have sufficient proof of being logged to Certificate Transparency (CT) servers. To help with the transition, we’ve released a series of improvements to our tools to verify and monitor CT compliance. READ MORE »
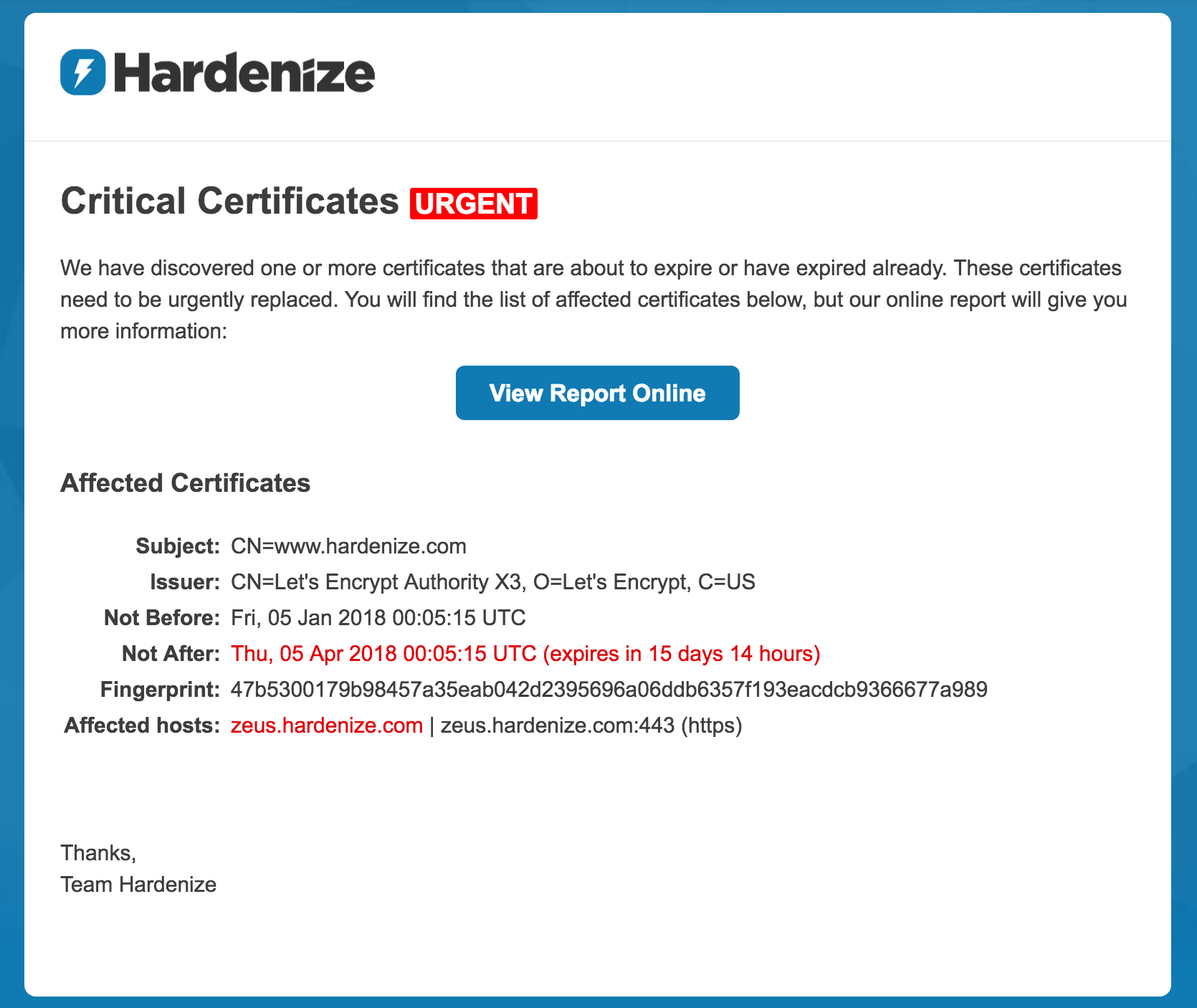
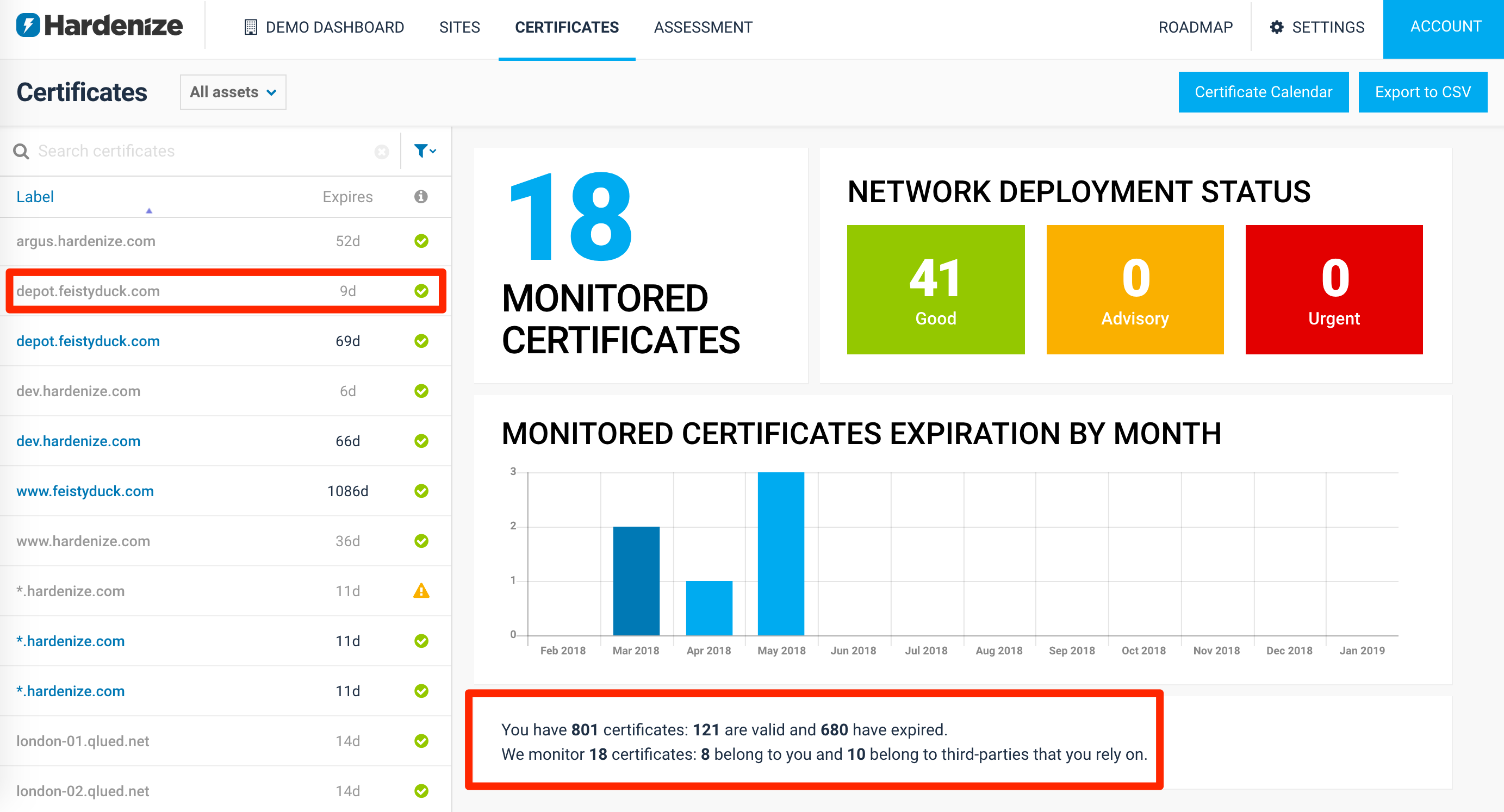
As of today, Hardenize officially supports daily notifications that alert you about certificates that are about to expire. Once a day we take a look at your properties and make a list of all certificates that haven’t been renewed. We include both your certificates as well as those that you rely on (e.g., third-party web sites, outsourced email servers, and so on). We then check every known network location once again to remove any certificates that have been renewed at the last minute. After that, if we’re left with any certificates on our list, we send you an email with a summary of all your affected properties and the corresponding network locations. READ MORE »
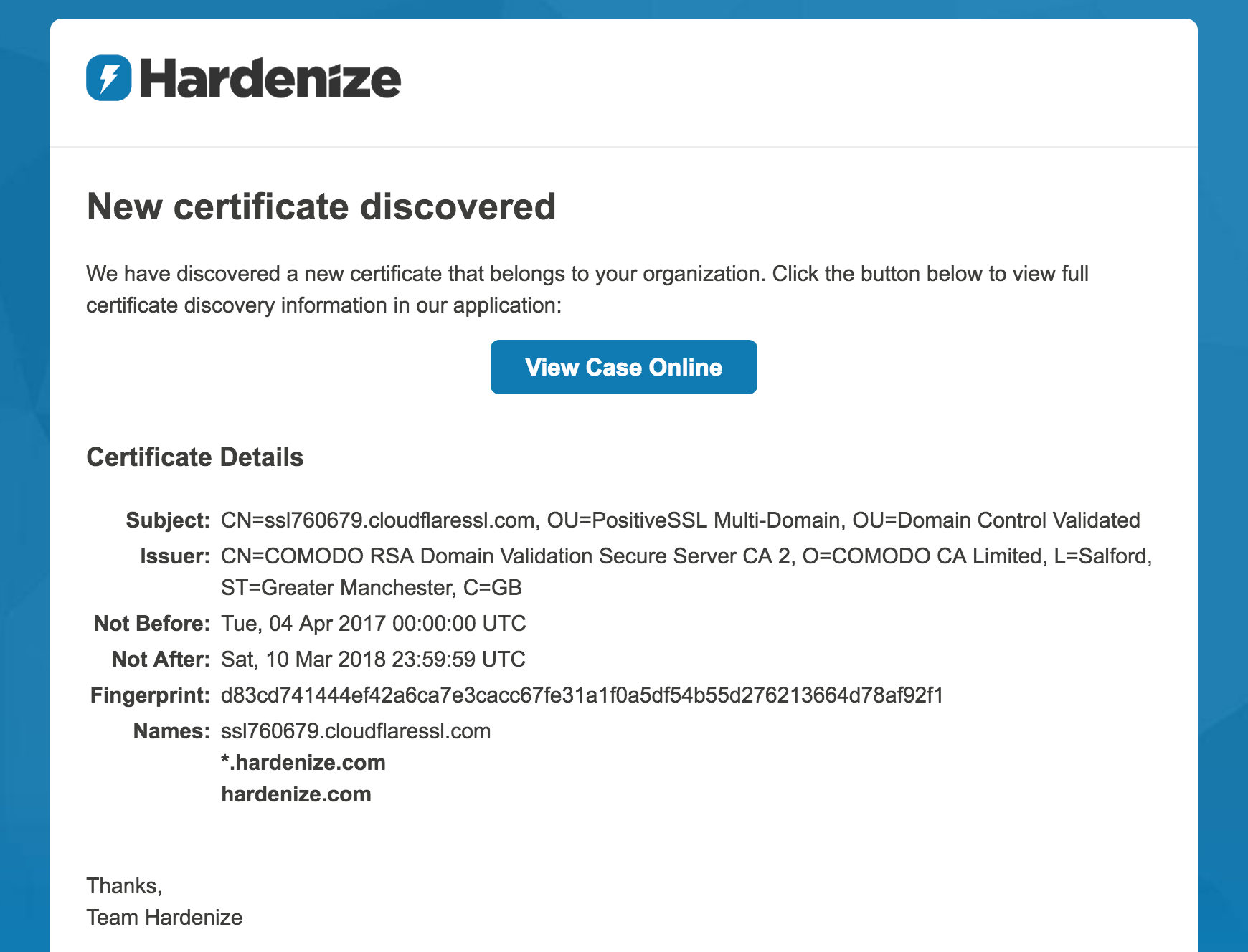
If you’re like me, you want to know about new certificates that are issued for your domain names. In fact, that’s the whole point of Certificate Transparency (CT), to be able to keep an eye on what Certification Authorities are doing in your name. Hardenize has supported real-time CT monitoring for several months already, but now we’ve added one simple yet very useful feature—email notifications for CT discoveries. READ MORE »
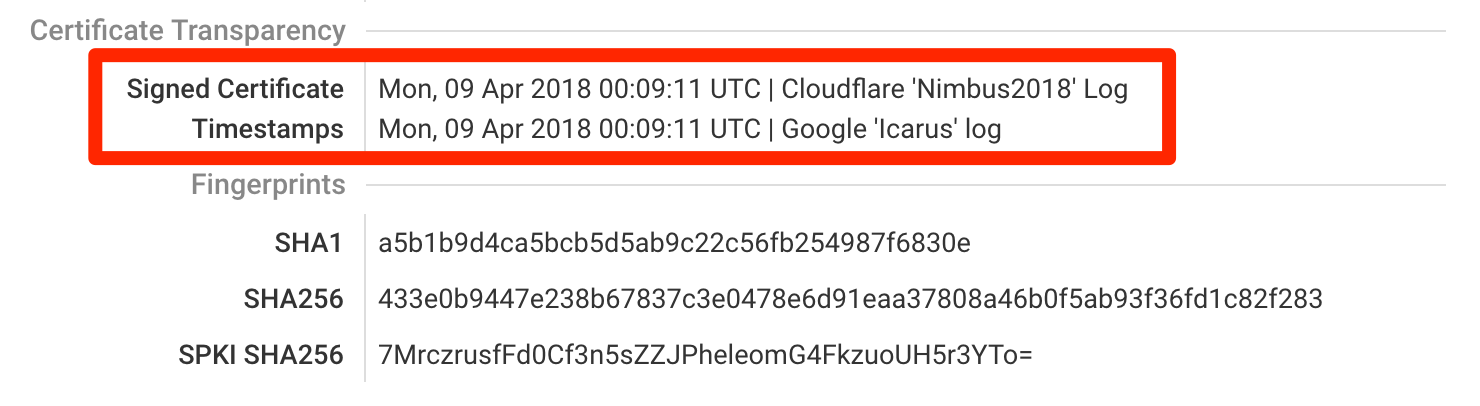
For our next key feature, we’re happy to announce a database of all public certificates recorded to Certificate Transparency logs. It’s another step we’re making toward building the best certificate inventory and CT monitoring tool ever. With the database seamlessly integrated with our product, our customers can now start with only a handful of domain names and have all their certificates in their accounts within seconds. This new database complements our existing real-time CT monitoring features. READ MORE »
Last month, in December, we decided to take advantage of a quieter month to make some bigger changes to our database and build a foundation for a number of new features. Today we’re releasing new functionality that adds teams, groups, multiple dashboards, and host management, all designed to make it easier to manage the information available in Hardenize accounts. READ MORE »
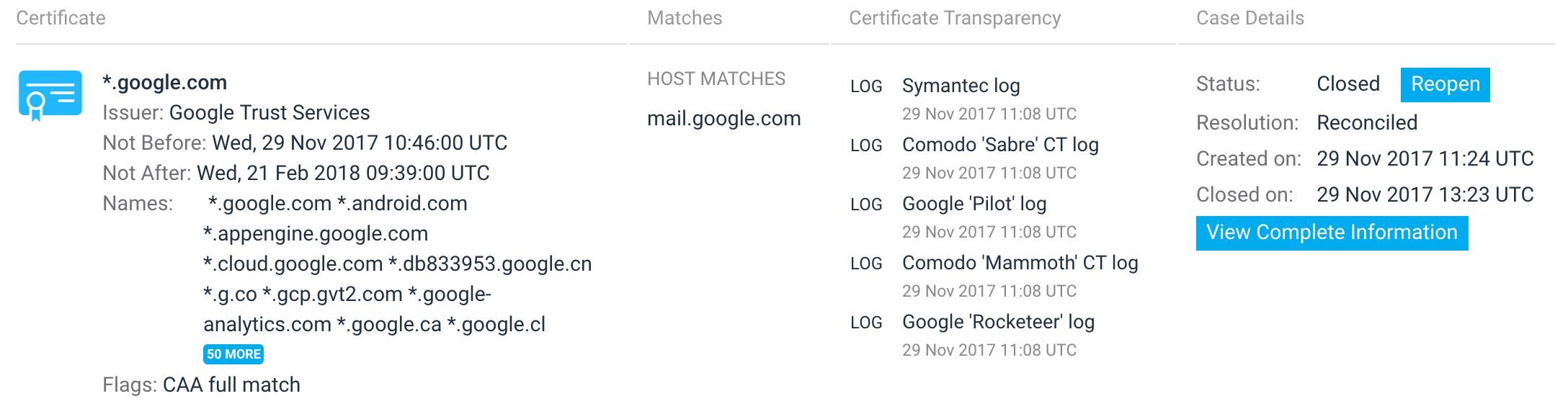
At Hardenize, we’re continuing to add new features on our path to the first commercial release. In an earlier blog post we talked about our certificate monitoring capabilities, which are based on network infrastructure scanning. Today, we’re taking the next step with the introduction of Certificate Transparency (CT) monitoring. This new feature is enabled for all our early customers. READ MORE »
Today we’re announcing a fun little project, our own security badge you can place on your web site to highlight your good security posture. I say fun, because working this project gave us an excuse to design an awesome-looking badge, but our motivation is really to help raise awareness of the importance of good security and make transparency the norm. READ MORE »


We are delighted to announce Hardenize Certificate Inventory and Monitoring, a significant new feature that we’ve just released. It’s enabled now for all our early customers. Certificate renewal has long been a pain point for organizations of all sizes. It’s rare to find someone who hasn’t had one of their certificates expire before they are replaced. With Hardenize we wish to ensure that never happens to you again. Equally important, we also wish to help you navigate the complex world of PKI. READ MORE »
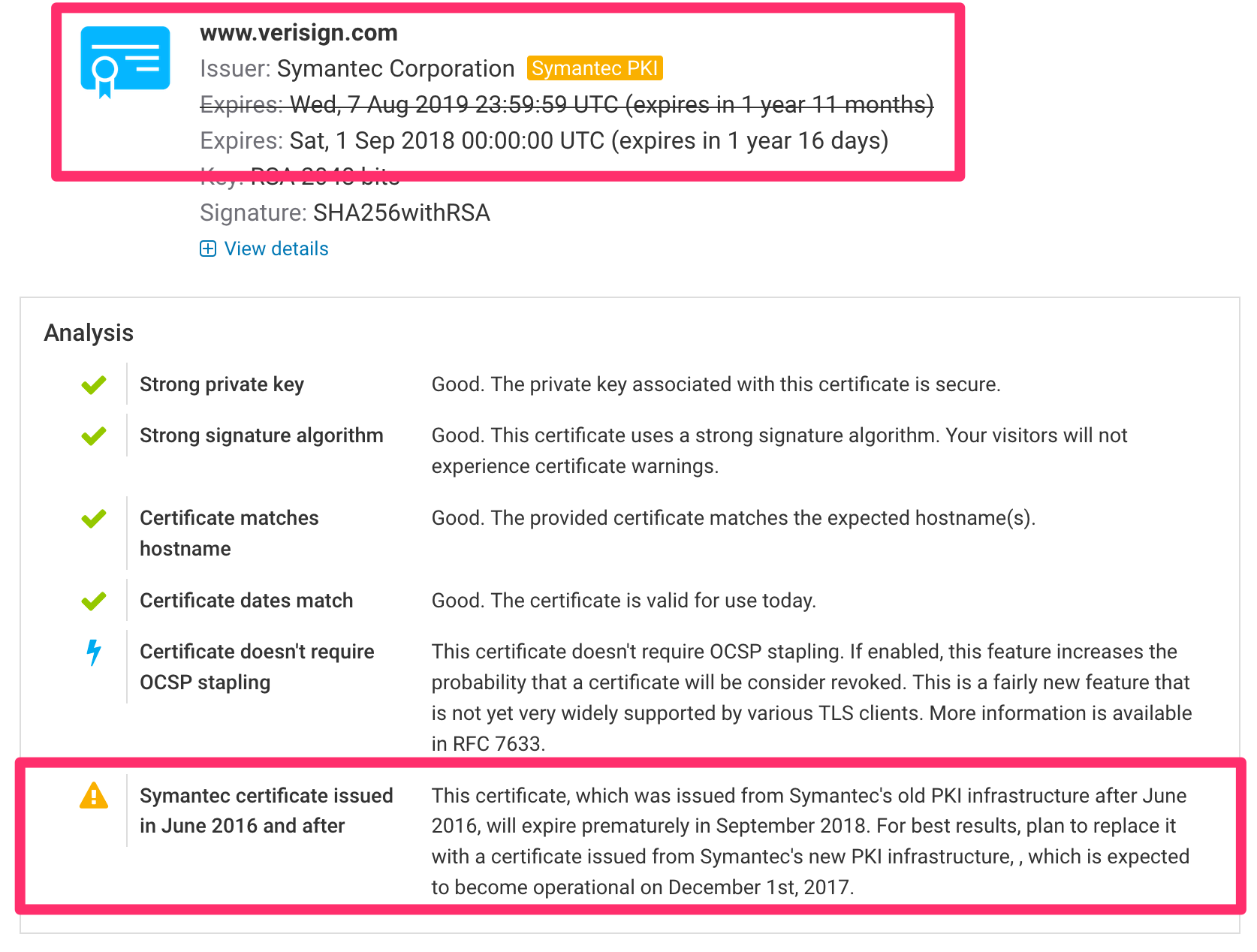
Google and Mozilla are planning to deprecate all existing Symantec certificates, cutting short their lifetime. This causes a significant operational problem for many organizations who will need to identify all affected certificates and then replace them before they are made invalid. To assist with this process, in Hardenize we’ve added detection of Symantec certificates (all brands) and we now present effective expiration dates. READ MORE »
Today we’re introducing a great new Hardenize feature—public dashboards. They are a great way to apply Hardenize’s complete assessment capabilities to a group of hosts and get a good understanding (quickly!) of what their security is like. We provide a summary page that shows the most important data points, but we also include the complete results for each of the participating sites individually. READ MORE »