

Welcome to the Hardenize blog. This is where we will document our journey as we make the Internet a more secure place and have some fun and excitement along the way.
As we build Hardenize, we spend our time designing exciting new features, which we like to call delighters. However, we also pay attention to what other important functionality we need, where we usually heed advice of our customers. Our most recent feature is one of those. We've just added support for two-factor authentication. To be honest, we're quite delighted to have it. So it's a win-win!
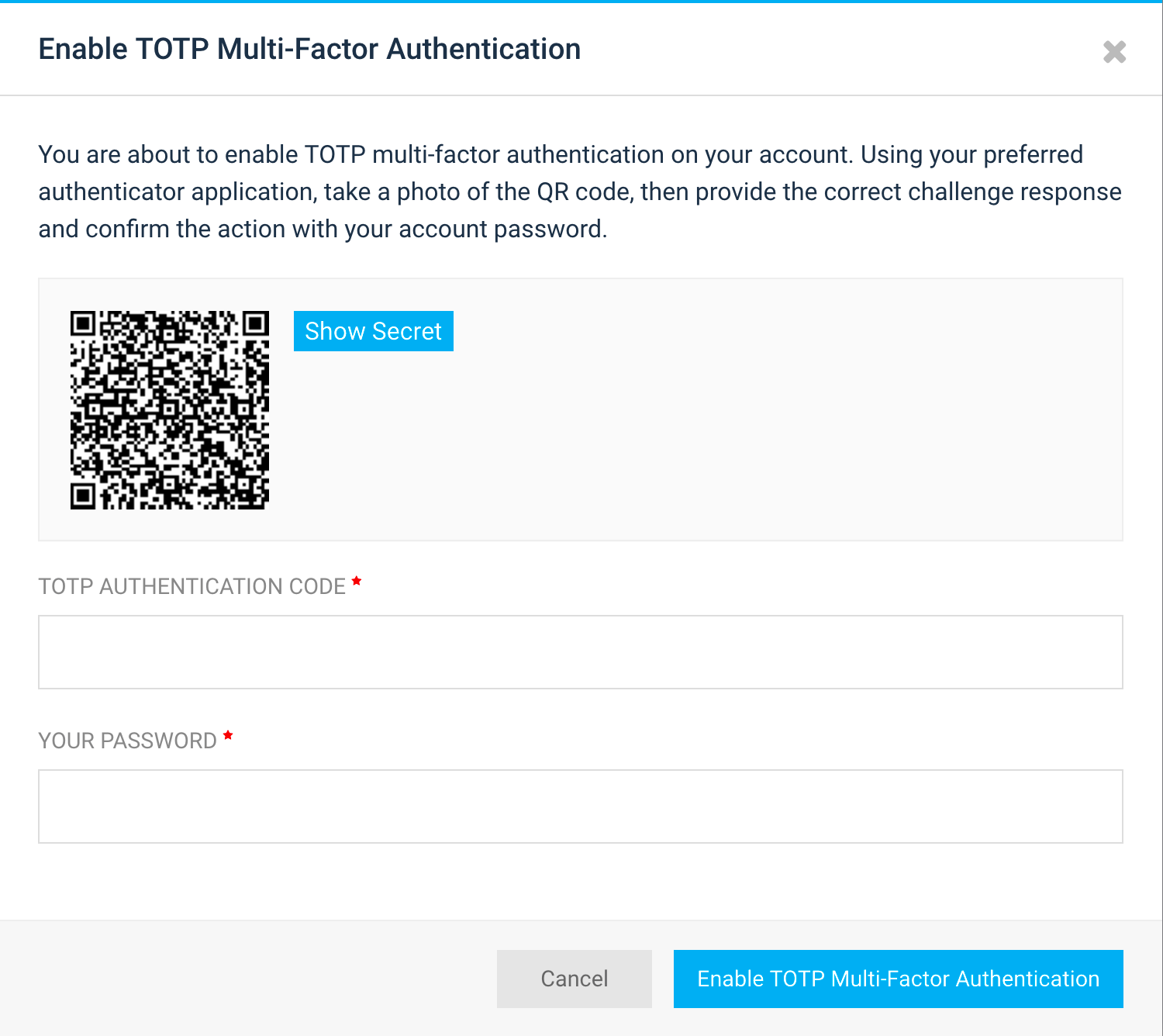
There are different ways in which two-factor authentication can be implemented. We decided to start with what's probably the most-widely used and secure method, via TOTP. Expanded, TOTP stands for Time-based one-Time Password, and it's specified in RFC 6238.
When TOTP-based two-factor authentication is enabled, a special TOTP secret is created by the server and shown to the user, usually in the form of a QR code. This is a quick method to communicate something that may otherwise be cumbersome to do manually. Later on, at sign in, after password authentication is successful, the user is asked to provide the second factor, which, in our case, is a 6-digit number that changes every 30 seconds. The end result is that the account remains safe even when the password is compromised, assuming the TOTP secret stays safe.
A great thing about two-factor authentication is that it also prevents attacks where the user's email account is compromised. To gain access, the attacker only needs to exercise the forgotten-password option, which of course all web sites have. With two-factor authentication, that attack no longer works.
Unfortunately, what also happens is that legitimate users can't recover their account if they lose their second factor. For this purpose, when we enable two-factor authentication for our users, we also create a set of recovery codes that can be used for backup. We hope that this mechanism will work in most situations, for example when a mobile phone breaks down or is stolen.
If all else fails, we've also added the option for organisation administrators to disable two-factor authentication for their users. This is very convenient, as they usually have a way to reach the users directly and verify their identity beforehand.