

Welcome to the Hardenize blog. This is where we will document our journey as we make the Internet a more secure place and have some fun and excitement along the way.
At Hardenize, we're continuing to add new features on our path to the first commercial release. In an earlier blog post we talked about our certificate monitoring capabilities, which are based on network infrastructure scanning. Today, we're taking the next step with the introduction of Certificate Transparency (CT) monitoring. This new feature is enabled for all our early customers.
CT integration brings many benefits, such as ability to discover all certificates used by your organization, no matter where they're installed. From there, we can ensure they're all deployed correctly and with appropriate TLS configuration. Monitoring also makes it possible to audit CAs worldwide, enforce internal issuance policies, and of course detect fraudulent certificates.
On top of what CT offers, we provide additional value by using what we know about your infrastructure to automatically handle routine activities. For example, there's no need to inform you about an appearance of a previously-known certificate in CT logs. Or—as in the case below—if you've deployed Certification Authority Authorization (CAA) and the certificate checks out, why not just tick the box for you?
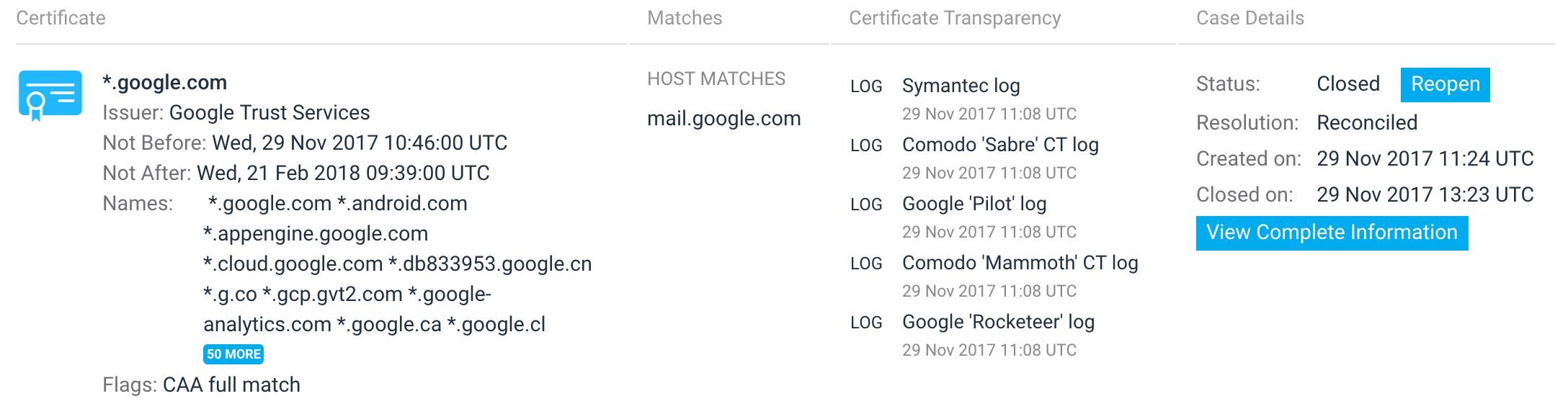
CT provides a wealth of data, but we want your job to be easier, not harder because of it. When you do need to manually review discovered certificates, we provide you with all the data you need to help you make your decision quickly. For example, we'll fetch all applicable CAA policies and show them to you on the same page with all other relevant data.
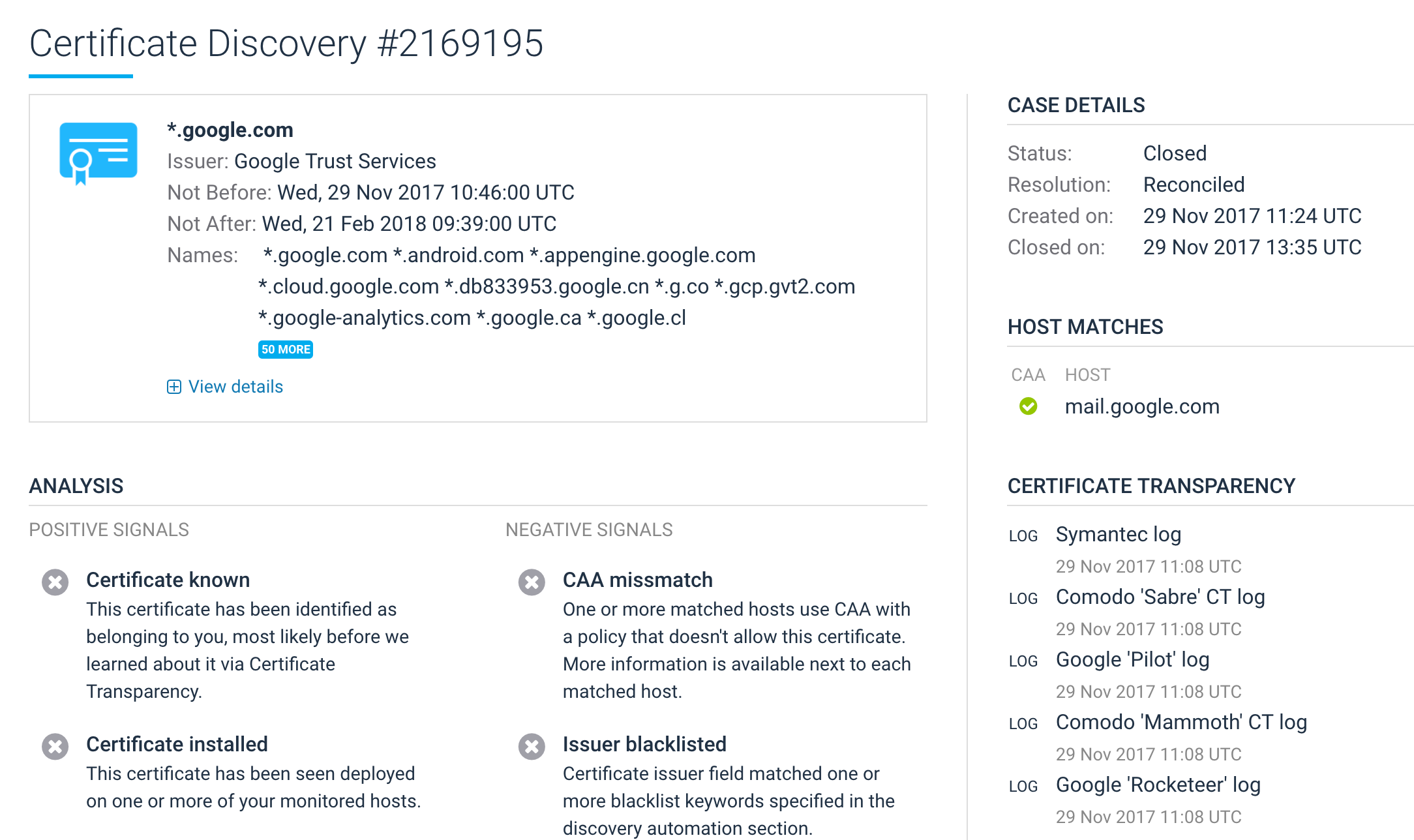
Actually, even if you are not using CAA, we support custom matching rules that can be used to whitelist and blacklist issuers. This is a great way to check a CAA policy before it's deployed and potentially causes disruption. For example, a strict whitelisting policy could escalate certificates from any issuer except those you allow.
The Internet relies on a trust model built on the concept of trusted third parties, which we call Certification Authorities (CAs). Conceptually, this approach is very simple: we're relying on a small number of vetted organizations to decide whom we should trust. From a technical perspective, this trust model is not great, but it's the only one we know how to deploy at scale so that it can be used by billions of people and machines every day.
In practice, the biggest weakness of the current system is the fact that any CA can issue a certificate for any web site in the world, even without consulting the domain name owner. Clearly, that's not right, but what can we do about? How can we improve our security without complicating the trust model too much so that it becomes unusable?
CT, promoted by Google, is a framework for auditing and monitoring of public certificates. The core idea is to make all publicly-trusted certificates public, creating a real-time stream of new certificates. With that, any interested party can audit CAs' operations as well as keep an eye on the certificates issued for their domain names.