

Welcome to the Hardenize blog. This is where we will document our journey as we make the Internet a more secure place and have some fun and excitement along the way.
We are delighted to announce Hardenize Certificate Inventory and Monitoring, a significant new feature that we’ve just released. It’s enabled now for all our early customers. Certificate renewal has long been a pain point for organizations of all sizes. It’s rare to find someone who hasn’t had one of their certificates expire before they are replaced. With Hardenize we wish to ensure that never happens to you again. Equally important, we also wish to help you navigate the complex world of PKI.
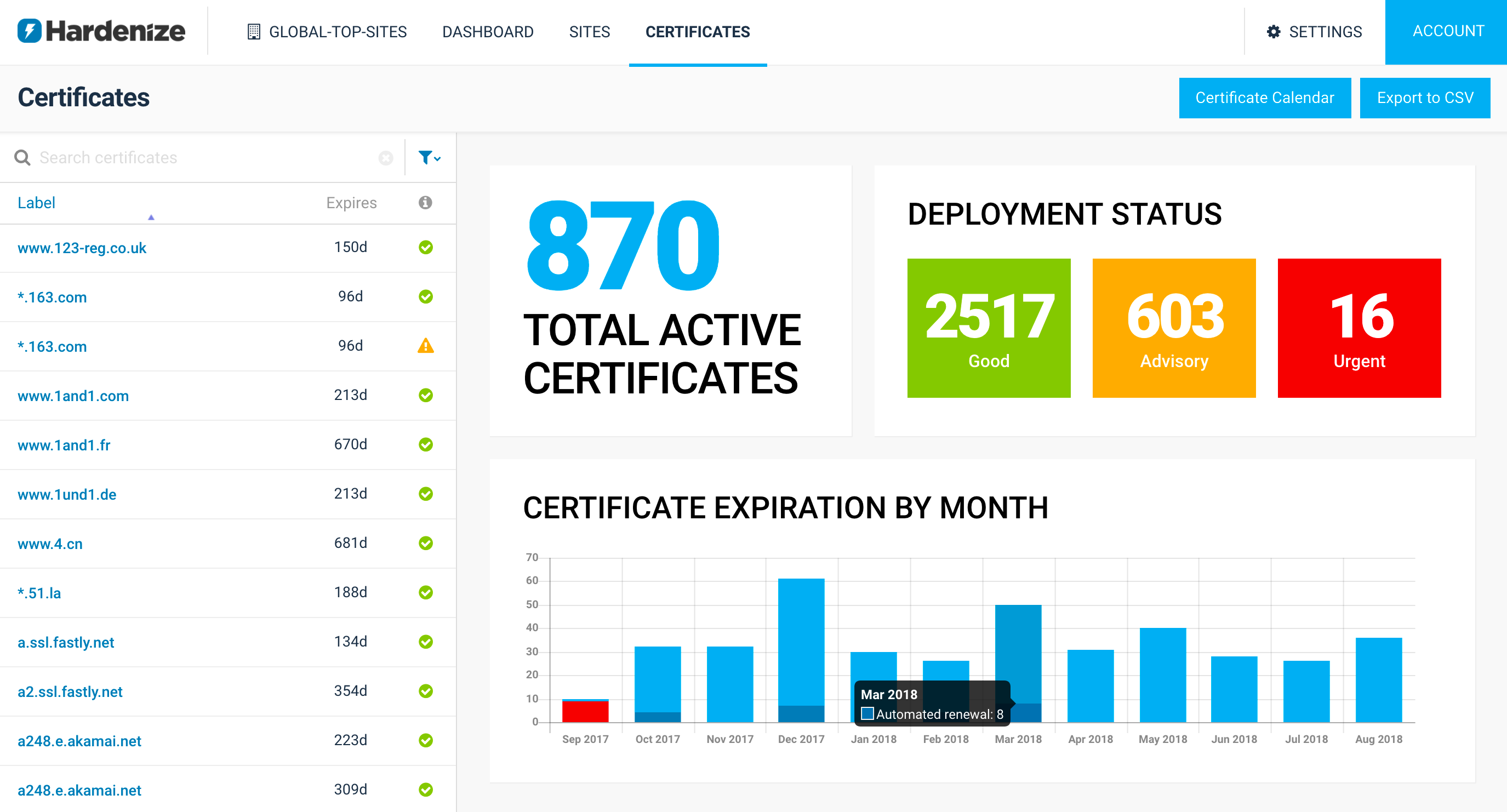
As if that hasn’t been difficult enough, recently we’ve seen a fair share of disruption with the WoSign and StartCom certification authorities, causing their certificates stop working before they are due. With Symantec, it’s going to be even more subtle. Last month we extended our reports to highlight certificates issued by Symantec PKI (many brands!), if you’re an organization of a non-trivial size, what you really need is to find all such certificates, no matter where they are. Even better, you may just want to treat them as all other certificates, but replace them before their effective expiration.
That said, we didn’t want to build just an expiration monitor; there are already many companies that do that. We wanted to take advantage of our PKI expertise to build a product that enables you to have a deeper understanding of how your certificates deployed, find edge cases before they affect you, and help you analyze what is effectively a PKI of you own.
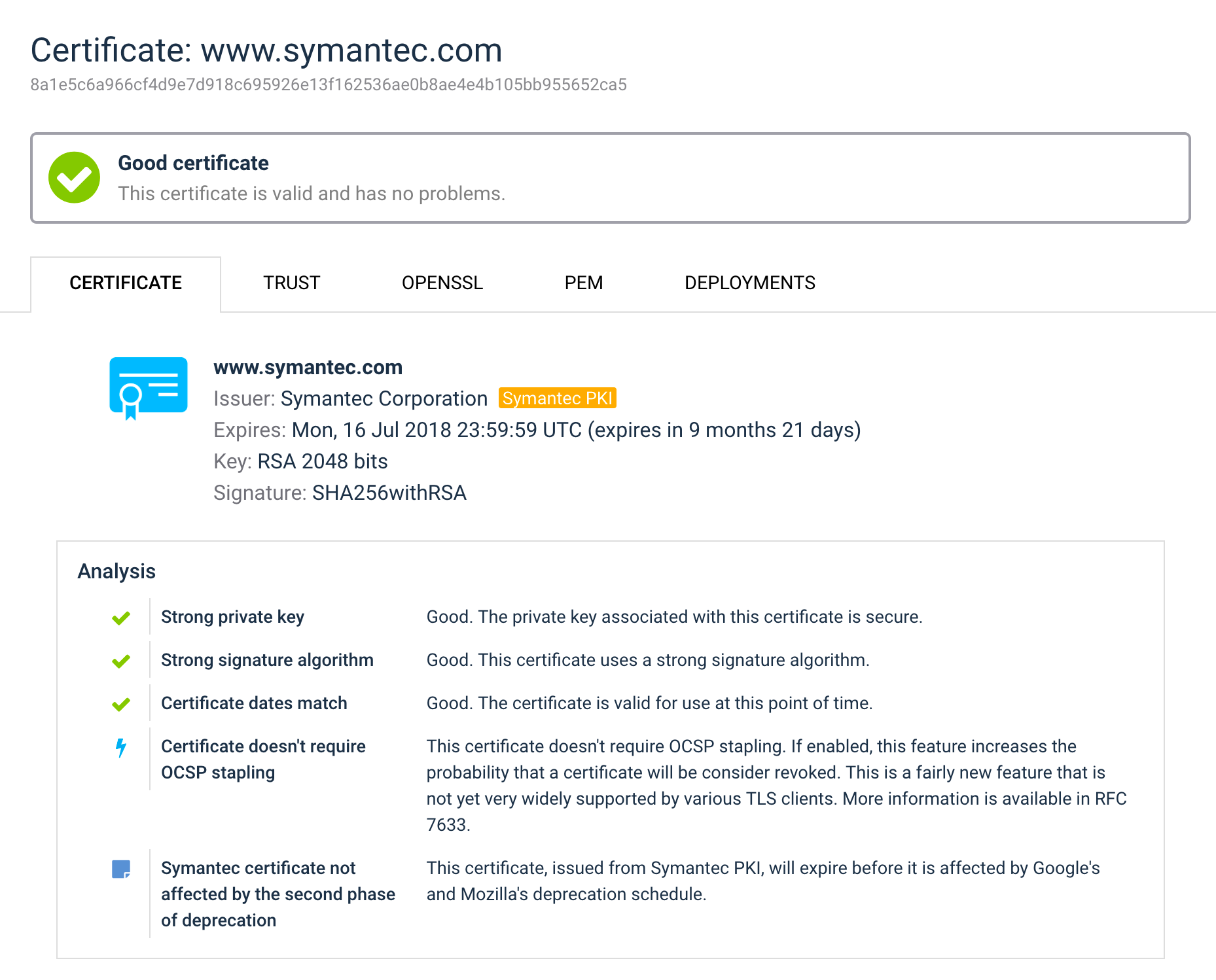
Here are some highlights from this release:
What we have today is immediately useful, but it’s just a starting point we wanted to use to start a discussion. In the following weeks we’ll be reaching out to our early customers to work with them to identify key functionality and implement it for them. We’ll be looking at features such as expiration notifications, reporting, improvements to certificate discovery and integration with Certificate Transparency. Exciting!