

Welcome to the Hardenize blog. This is where we will document our journey as we make the Internet a more secure place and have some fun and excitement along the way.
“What’s running on our assets?” is often the next question our customers ask once they’ve successfully built an inventory of their domains, hosts, certificates, IP addresses, and cloud resources that is kept up to date continuously and automatically. To help our customers answer this, we’re delighted to announce Technologies V1 which is available now at no additional charge to paying customers.
The frameworks, libraries, and services used in websites today are wide ranging in scope. Whether it’s the languages used to build the application, or the advertising, payment processing, and content management systems used to run a business, the technologies used adds another layer of complexity to the attack surface. Security teams should have visibility of this as, and knowing what is being used where is a critical part of identifying exposure as part of the scoping stage of a CTEM programme.
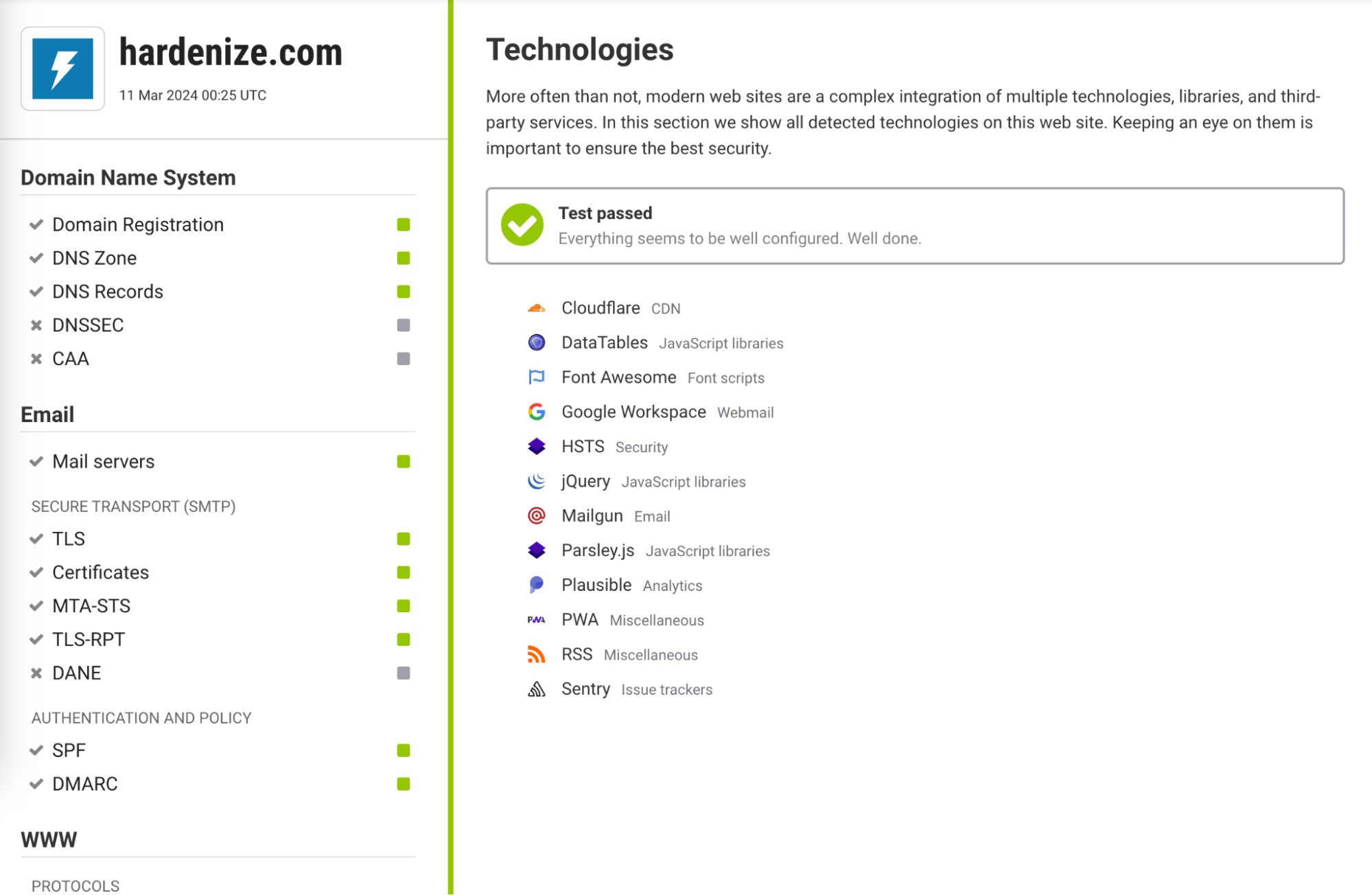
During our assessment process, if HTTP or HTTPS is found on a host, then our headless browser will detect then display the web page itself and the technologies, libraries and third-party services used on it. We find technologies in more than 100 different categories. The technology found and the category will be displayed on the host assessment, and has also been added to the downloadable PDF assessment.