

No one wants to spend their time populating databases. We draw from multiple sources of information to maintain a search engine that can help you find your web sites. We rely on this search engine initially during the onboarding process so that you can get results quickly. Later, as you continue to use Hardenize, we search in the background to find new properties that belong to you and automatically add them to your inventory.
Additionally, we support managed cloud integrations, enabling you to connect your Hardenize account to your AWS, Azure, GCP, and other cloud accounts.
We maintain a database that contains all the world's domains and subdomains. Our keyword-based discovery not only finds the properties that belong to you, but also continuously checks for substrings and malicious obfuscated variations that you should be aware of.
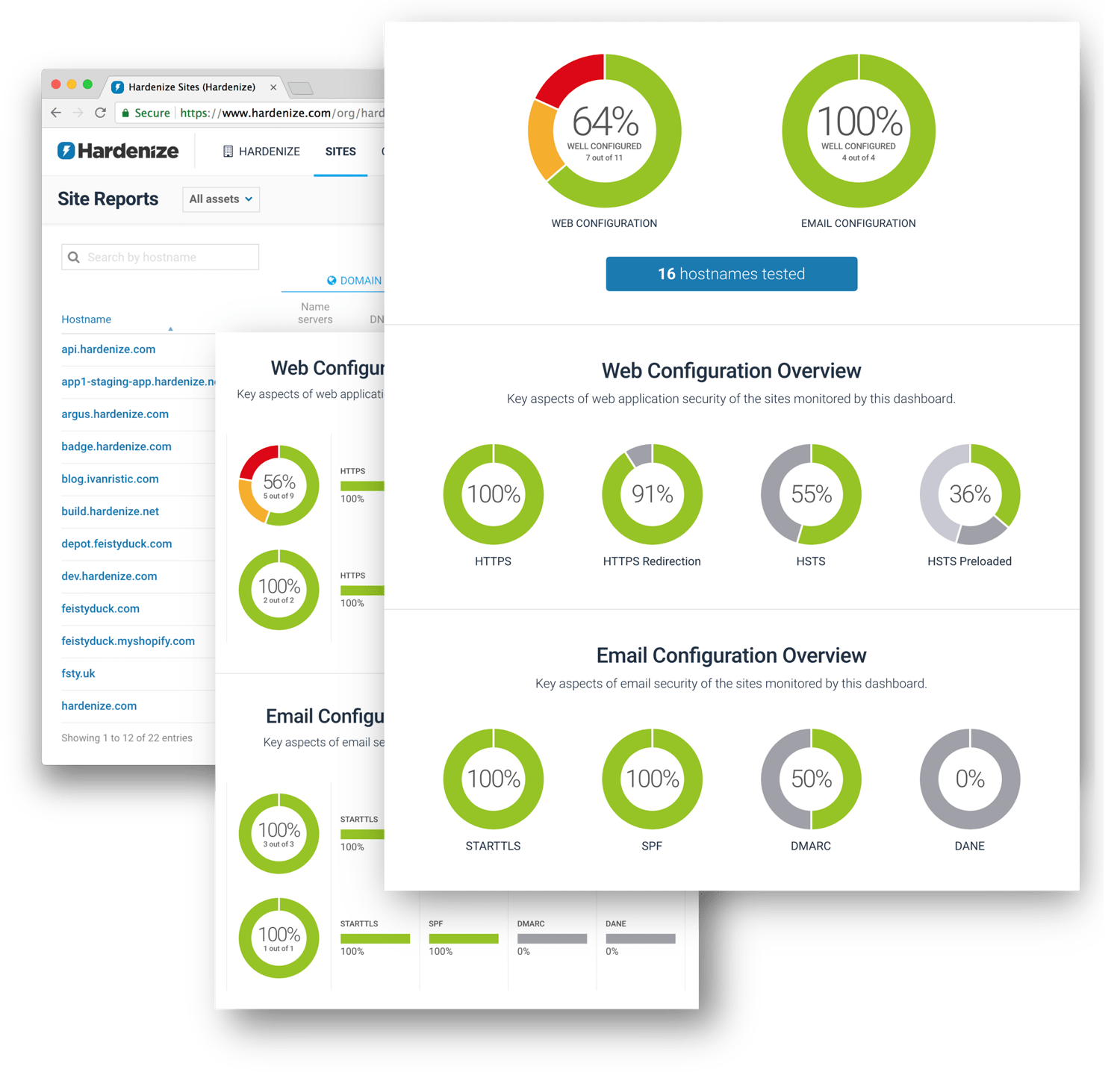
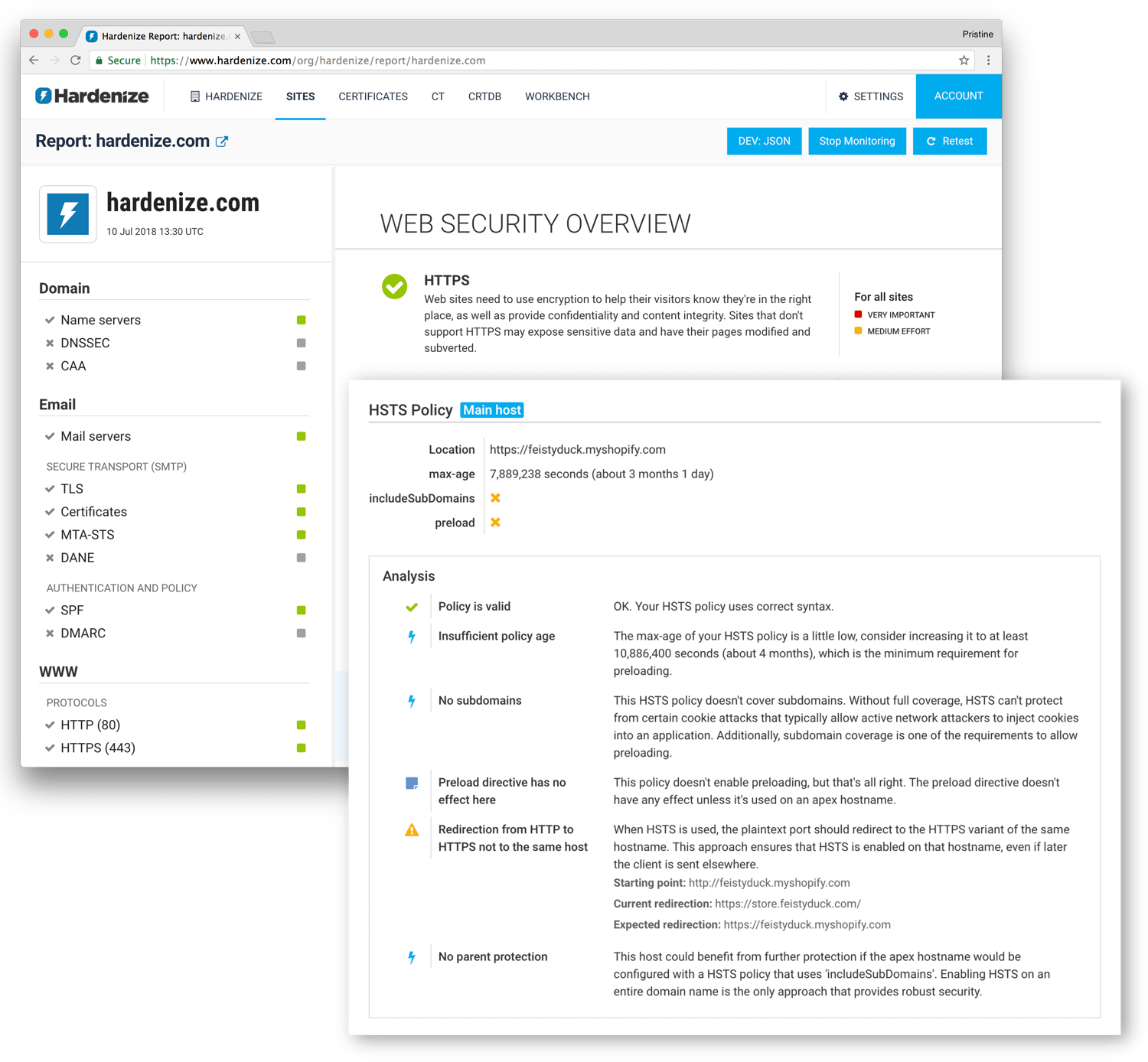
We continuously monitor your entire network perimeter with fresh data available on a daily basis. We combine scanning of domains, hostnames, and IP addresses. Our network scanning covers the top 2,000 TCP and UDP ports.
Today, unlike maybe a decade ago, we have the standards we need to properly secure our properties. However, keeping up with the developments and learning how to use all available and necessary technologies correctly is proving difficult. We've made it our job to understand all the network and security standards so that you don't have to.
We have a decade of experience building tools for deep analysis of security and network configuration. Our approach is to evaluate service properties in context and as a whole, looking at how everything fits together. In other words, we build tools that work like humans. Crucially, we don't look for bad things. Instead, we answer the question if something is correctly and securely configured.
Ironically, it's never been more difficult to deploy certificates correctly. Today, you can have a certificate that's valid on the surface, but can fail due to external factors, for example deprecation of Symantec certificates. We understand these problems and correctly alert to certificate configuration problems.
We monitor your certificates and notify you if they're about to expire, avoiding downtime. Crucially, we also monitor the certificates of third-party services your sites rely on, helping you avoid problems via dependencies and services you don't control directly.
Via Certificate Transparency, we observe all the world's certificates as they are issued in real time. We detect those that belong to you and we pull them into your account. We automate analysis of these discoveries so that you can ignore those that are known and compliant, but focus your attention on misissued certificates.
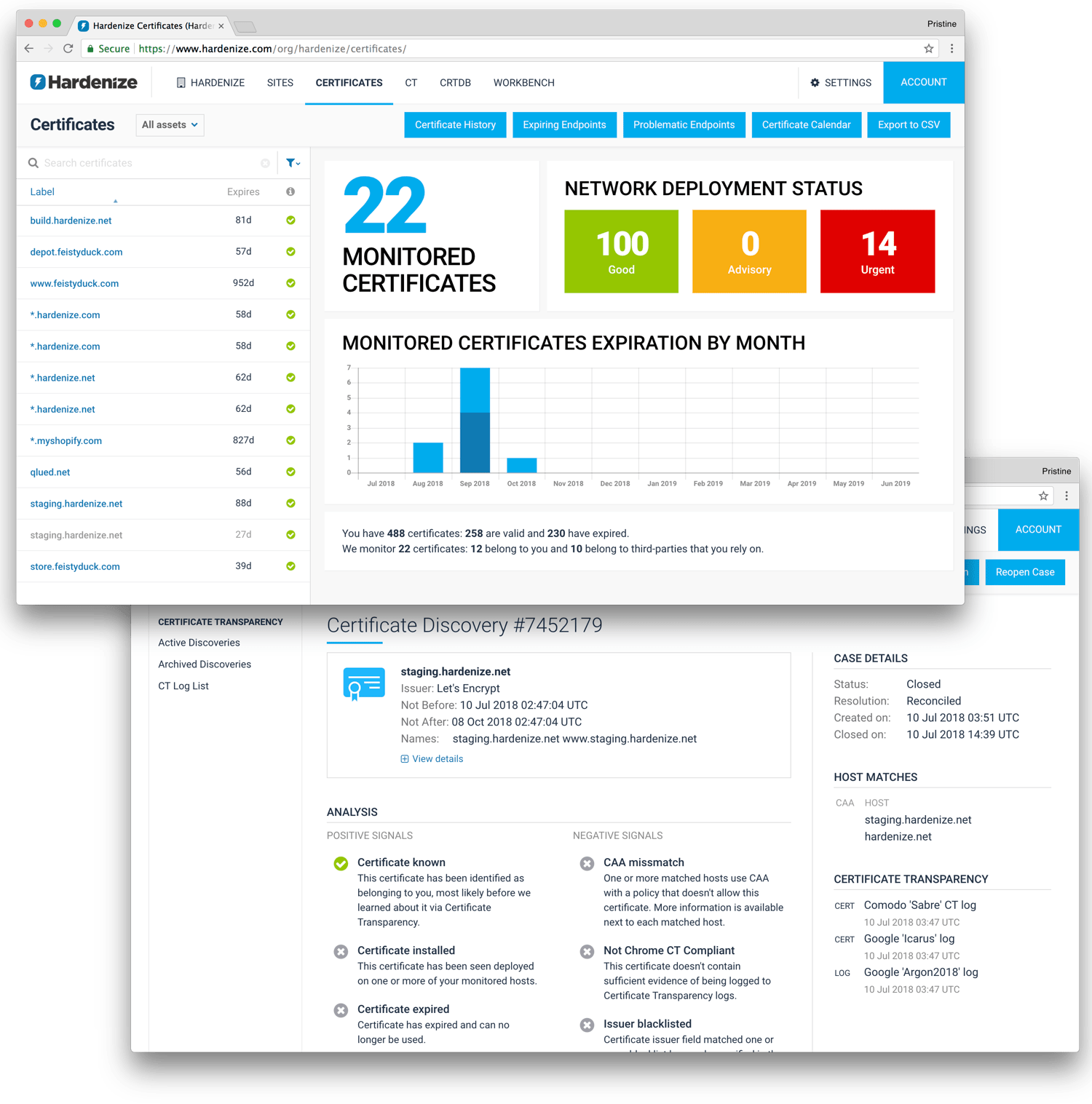







Hardenize is provided as a service running in the cloud. There's nothing to install or manage, which means that you can start using our product in minutes and always have the latest version of our software.
Categorize hosts into groups and create multiple dashboards. Create multiple user accounts with different access levels and assign them to teams. Then assign host groups to teams to indicate responsibility.
Check for all known SSL and TLS protocols, cipher suites, named groups, and other cryptographic primitives. Simulate connections from popular clients to understand what they will negotiate with your sites.
Ensure your certificates work in major trust stores. Receive expiration notifications. Find deprecated Symantec certificates. Use CAA to control who can issue certificates.
Monitor certificates issued for your properties worldwide, in real-time. Automatically handle routine discoveries, but highlight policy violations and misissued certificates.
Deploy all the relevant standards, such as HSTS, CSP, SRI, Expect-CT, and others. Use secure cookies, including name prefixes and same-site cookies. Prevent mixed content.
Check for STARTTLS and correct TLS and PKI configuration. Deploy SPF and DMARC with confidence. Prepare for new standards, such as MTA-STS and TLSRPT.
Monitor your DNS and DNSSEC configuration across IPv4 and IPv6 networks. Find all IP addresses that provide a service. Deploy and validate DANE.
Use our APIs to programmatically manage your account. Integrate with our events subsystem to receive real-time notifications.